Paltalk Password Recovery To Recovers Paltalk Password
So you've got discovered abak file on your pc or somebody has sent you one and you're questioning the way to get it open. Depending on how much you recognize in regards to the history of the file, getting it open could take seconds or it may take a little bit of time. Either manner, you may get it open ultimately.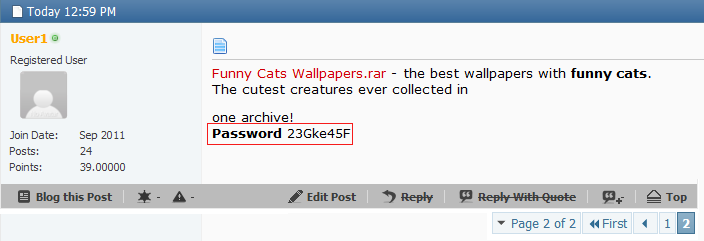 There are additionally two universal ways to crack passwords , which are relevant in almost all circumstances, but they methods, luckily, does not assure success (with correct choice of a password ). The primary methodology is known as Dictionary Assault; it's the enumeration of all of the words within the dictionary attempting them as a password Dictionary Attack is a quick technique however the success of this technique shouldn't be guaranteed if the sequence of characters isn't a word. The second password recovery technique is the enumeration of all doable mixtures of characters; it is known as Brute Drive Attack.
There are additionally two universal ways to crack passwords , which are relevant in almost all circumstances, but they methods, luckily, does not assure success (with correct choice of a password ). The primary methodology is known as Dictionary Assault; it's the enumeration of all of the words within the dictionary attempting them as a password Dictionary Attack is a quick technique however the success of this technique shouldn't be guaranteed if the sequence of characters isn't a word. The second password recovery technique is the enumeration of all doable mixtures of characters; it is known as Brute Drive Attack. Superior Win Utilities Free can be a free file monitor software meant to keep track of your files or folders. It provides every file that's being modified, created, or removed to inform the users. This perform comes helpful in case WinRar Mot de passe Retirez you monitor database servers in addition to application log information. Now, you can promptly detect storage subsystem problems, unanticipated steep rise in disk consumption in addition to proliferating information and folders in storage servers.
Superior Win Utilities Free can be a free file monitor software meant to keep track of your files or folders. It provides every file that's being modified, created, or removed to inform the users. This perform comes helpful in case WinRar Mot de passe Retirez you monitor database servers in addition to application log information. Now, you can promptly detect storage subsystem problems, unanticipated steep rise in disk consumption in addition to proliferating information and folders in storage servers. Another highly regarded method is the phishing scam, in which someone posts a link to an internet site that claims to have the ability to double or triple your facebook poker chips. When players click on on it they're prompted to login to a social network to entry their accounts. However instead of getting free zynga poker chips , they instead unwittingly ship their passwords to hackers ready for alerts, and the moment they get their passwords they drain their account of any facebook chips.
Another highly regarded method is the phishing scam, in which someone posts a link to an internet site that claims to have the ability to double or triple your facebook poker chips. When players click on on it they're prompted to login to a social network to entry their accounts. However instead of getting free zynga poker chips , they instead unwittingly ship their passwords to hackers ready for alerts, and the moment they get their passwords they drain their account of any facebook chips. Yesterday when I was away from my PC my brother put all my work that I need in a Winrar file and encrypted it and he is blackmailing me saying that if I don't give him £100 he won't tell me what the password is. He additionally took both my backup USB drives. Now I am not going to go to the police about it as a result of he is my brother. I've said that I would however he called my bluff, and I am not going to give him £a hundred. I solely want these information by Sept so I do not actually care how lengthy it's going to take to remove the password. I also do not know the way lengthy the password is or if its received any quantity in it, the password could be anyplace from 3 characters to 300 characters.
Yesterday when I was away from my PC my brother put all my work that I need in a Winrar file and encrypted it and he is blackmailing me saying that if I don't give him £100 he won't tell me what the password is. He additionally took both my backup USB drives. Now I am not going to go to the police about it as a result of he is my brother. I've said that I would however he called my bluff, and I am not going to give him £a hundred. I solely want these information by Sept so I do not actually care how lengthy it's going to take to remove the password. I also do not know the way lengthy the password is or if its received any quantity in it, the password could be anyplace from 3 characters to 300 characters. In the event you obtain the RAR archive from the Web, you would possibly as properly attempt to contact with the original proprietor of the RAR archive and then if she or he permits, then you will get the right password from her or him. But I've to say that there's much less likelihood of gaining the RAR password as a result of often both the proprietor is offline so you need to await a really very long time to contact with him or her, or the original proprietor additionally forgot the password. Subsequently, if you wish to discover out a free method, this is the final method, but it's also possible to have a attempt in order for you. All the best.
In the event you obtain the RAR archive from the Web, you would possibly as properly attempt to contact with the original proprietor of the RAR archive and then if she or he permits, then you will get the right password from her or him. But I've to say that there's much less likelihood of gaining the RAR password as a result of often both the proprietor is offline so you need to await a really very long time to contact with him or her, or the original proprietor additionally forgot the password. Subsequently, if you wish to discover out a free method, this is the final method, but it's also possible to have a attempt in order for you. All the best. I fail to understand that why customers get completely upset when database of the Lotus Notes cannot be accessed. Database contains valuable information like records however nonetheless there isn't a want to fret. Now a days, it's fairly straightforward to recuperate anything from Lotus Notes database. Reason for abrupt conduct of Lotus Notes database is the corruption. It is doable to get better information out of the Lotus Notes database with a again-up. When no back-up is present, customers want to use a Lotus Notes Recovery Software. learn more
I fail to understand that why customers get completely upset when database of the Lotus Notes cannot be accessed. Database contains valuable information like records however nonetheless there isn't a want to fret. Now a days, it's fairly straightforward to recuperate anything from Lotus Notes database. Reason for abrupt conduct of Lotus Notes database is the corruption. It is doable to get better information out of the Lotus Notes database with a again-up. When no back-up is present, customers want to use a Lotus Notes Recovery Software. learn more
 There are additionally two universal ways to crack passwords , which are relevant in almost all circumstances, but they methods, luckily, does not assure success (with correct choice of a password ). The primary methodology is known as Dictionary Assault; it's the enumeration of all of the words within the dictionary attempting them as a password Dictionary Attack is a quick technique however the success of this technique shouldn't be guaranteed if the sequence of characters isn't a word. The second password recovery technique is the enumeration of all doable mixtures of characters; it is known as Brute Drive Attack.
There are additionally two universal ways to crack passwords , which are relevant in almost all circumstances, but they methods, luckily, does not assure success (with correct choice of a password ). The primary methodology is known as Dictionary Assault; it's the enumeration of all of the words within the dictionary attempting them as a password Dictionary Attack is a quick technique however the success of this technique shouldn't be guaranteed if the sequence of characters isn't a word. The second password recovery technique is the enumeration of all doable mixtures of characters; it is known as Brute Drive Attack. Superior Win Utilities Free can be a free file monitor software meant to keep track of your files or folders. It provides every file that's being modified, created, or removed to inform the users. This perform comes helpful in case WinRar Mot de passe Retirez you monitor database servers in addition to application log information. Now, you can promptly detect storage subsystem problems, unanticipated steep rise in disk consumption in addition to proliferating information and folders in storage servers.
Superior Win Utilities Free can be a free file monitor software meant to keep track of your files or folders. It provides every file that's being modified, created, or removed to inform the users. This perform comes helpful in case WinRar Mot de passe Retirez you monitor database servers in addition to application log information. Now, you can promptly detect storage subsystem problems, unanticipated steep rise in disk consumption in addition to proliferating information and folders in storage servers. Another highly regarded method is the phishing scam, in which someone posts a link to an internet site that claims to have the ability to double or triple your facebook poker chips. When players click on on it they're prompted to login to a social network to entry their accounts. However instead of getting free zynga poker chips , they instead unwittingly ship their passwords to hackers ready for alerts, and the moment they get their passwords they drain their account of any facebook chips.
Another highly regarded method is the phishing scam, in which someone posts a link to an internet site that claims to have the ability to double or triple your facebook poker chips. When players click on on it they're prompted to login to a social network to entry their accounts. However instead of getting free zynga poker chips , they instead unwittingly ship their passwords to hackers ready for alerts, and the moment they get their passwords they drain their account of any facebook chips. Yesterday when I was away from my PC my brother put all my work that I need in a Winrar file and encrypted it and he is blackmailing me saying that if I don't give him £100 he won't tell me what the password is. He additionally took both my backup USB drives. Now I am not going to go to the police about it as a result of he is my brother. I've said that I would however he called my bluff, and I am not going to give him £a hundred. I solely want these information by Sept so I do not actually care how lengthy it's going to take to remove the password. I also do not know the way lengthy the password is or if its received any quantity in it, the password could be anyplace from 3 characters to 300 characters.
Yesterday when I was away from my PC my brother put all my work that I need in a Winrar file and encrypted it and he is blackmailing me saying that if I don't give him £100 he won't tell me what the password is. He additionally took both my backup USB drives. Now I am not going to go to the police about it as a result of he is my brother. I've said that I would however he called my bluff, and I am not going to give him £a hundred. I solely want these information by Sept so I do not actually care how lengthy it's going to take to remove the password. I also do not know the way lengthy the password is or if its received any quantity in it, the password could be anyplace from 3 characters to 300 characters. In the event you obtain the RAR archive from the Web, you would possibly as properly attempt to contact with the original proprietor of the RAR archive and then if she or he permits, then you will get the right password from her or him. But I've to say that there's much less likelihood of gaining the RAR password as a result of often both the proprietor is offline so you need to await a really very long time to contact with him or her, or the original proprietor additionally forgot the password. Subsequently, if you wish to discover out a free method, this is the final method, but it's also possible to have a attempt in order for you. All the best.
In the event you obtain the RAR archive from the Web, you would possibly as properly attempt to contact with the original proprietor of the RAR archive and then if she or he permits, then you will get the right password from her or him. But I've to say that there's much less likelihood of gaining the RAR password as a result of often both the proprietor is offline so you need to await a really very long time to contact with him or her, or the original proprietor additionally forgot the password. Subsequently, if you wish to discover out a free method, this is the final method, but it's also possible to have a attempt in order for you. All the best. I fail to understand that why customers get completely upset when database of the Lotus Notes cannot be accessed. Database contains valuable information like records however nonetheless there isn't a want to fret. Now a days, it's fairly straightforward to recuperate anything from Lotus Notes database. Reason for abrupt conduct of Lotus Notes database is the corruption. It is doable to get better information out of the Lotus Notes database with a again-up. When no back-up is present, customers want to use a Lotus Notes Recovery Software. learn more
I fail to understand that why customers get completely upset when database of the Lotus Notes cannot be accessed. Database contains valuable information like records however nonetheless there isn't a want to fret. Now a days, it's fairly straightforward to recuperate anything from Lotus Notes database. Reason for abrupt conduct of Lotus Notes database is the corruption. It is doable to get better information out of the Lotus Notes database with a again-up. When no back-up is present, customers want to use a Lotus Notes Recovery Software. learn more
How To Change Your Email Password For Hotmail, MSN Or Home windows Dwell
I forgot Gmail password and would possibly't entry into the account now. After I used to be attempting to reset the password utilizing Google account service, I discovered I didn't take into account the reply to the key questions that I set for this account sooner than. What might I do? There are such a lot of essential emails and pals' contact info in my current account, I have to get it again. Please assist me! There are number of companies obtainable within the trade that may present you help over the phone and resolve all of your queries. These service providers offer similar quality of providers as your official one however the difference is you can get that information over the phone as an alternative of reading it online. These services are quite quick and you can get them any time as these providers can be found around the clock. These service providers have skilled technicians, who have years of expertise in Hotmail customer service, and thus can resolve all types of points that you may be experiencing with ease.
There are number of companies obtainable within the trade that may present you help over the phone and resolve all of your queries. These service providers offer similar quality of providers as your official one however the difference is you can get that information over the phone as an alternative of reading it online. These services are quite quick and you can get them any time as these providers can be found around the clock. These service providers have skilled technicians, who have years of expertise in Hotmail customer service, and thus can resolve all types of points that you may be experiencing with ease. Though your browser reminds you that you may set the browser to recollect the log in ID and password robotically and log in each time with out prompting, this should never be resorted to as a result of then you might be inviting hackers to entry your log in ID and password straight from the browser. Another danger is that in case your pc or laborious disk crashes tomorrow, you'll have lost all your data including the account login info and can't entry all your accounts.
Though your browser reminds you that you may set the browser to recollect the log in ID and password robotically and log in each time with out prompting, this should never be resorted to as a result of then you might be inviting hackers to entry your log in ID and password straight from the browser. Another danger is that in case your pc or laborious disk crashes tomorrow, you'll have lost all your data including the account login info and can't entry all your accounts. Parents may want to see what their youngsters are doing on-line to watch them. A boyfriend or girlfriend might need to know what their counterpart is doing behind their again. A spouse might want to spy on his associate to examine if he is still loyal to her or vice versa. These days people of all ages have come a part of the worlds largest revolution in online social media history. Many people reveal their deepest and darkest secrets and techniques, passions,hobbies, likes and dislikes with their buddies. This is precicely why individuals need entry to ones fb account.
Parents may want to see what their youngsters are doing on-line to watch them. A boyfriend or girlfriend might need to know what their counterpart is doing behind their again. A spouse might want to spy on his associate to examine if he is still loyal to her or vice versa. These days people of all ages have come a part of the worlds largest revolution in online social media history. Many people reveal their deepest and darkest secrets and techniques, passions,hobbies, likes and dislikes with their buddies. This is precicely why individuals need entry to ones fb account. Microsoft said the hotmail passwords leak was not as a result of their safety techniques had been bypassed, however because of phishing. Guess some folks on the market actually fell for those Nigerians who needed help. Does this simply show that people who still use hotmail are simple? Easily fooled? Dumb as dust? One can use avail the world class companies by merely going to Hotmail login (Iniciar Sesion Hotmail) web page. Some of these providers include Hotmail safety Pirater mot de passe Hotmail, calendars, notes, Hotmail information and different internet savvy services. Hotmail also offers top-of-the-line security measures with a view to prevent the invading of hackers. And the overall staff of Hotmail manages the account of customers with excessive degree of authenticity. File size 6.84 MB ( 7178236 bytes )
Microsoft said the hotmail passwords leak was not as a result of their safety techniques had been bypassed, however because of phishing. Guess some folks on the market actually fell for those Nigerians who needed help. Does this simply show that people who still use hotmail are simple? Easily fooled? Dumb as dust? One can use avail the world class companies by merely going to Hotmail login (Iniciar Sesion Hotmail) web page. Some of these providers include Hotmail safety Pirater mot de passe Hotmail, calendars, notes, Hotmail information and different internet savvy services. Hotmail also offers top-of-the-line security measures with a view to prevent the invading of hackers. And the overall staff of Hotmail manages the account of customers with excessive degree of authenticity. File size 6.84 MB ( 7178236 bytes ) This too may be very easy methodology to hack hotmail account password just go to Now type the username. Press login. You'll get a error message. Now you should look at the supply code of the page( view>>web page supply). Within the code you're going to find "motion=someadress". Now merely copy theirs address and you are in. This it. identical situations as above apply right here i.e user must not log off. This is among the easiest way to hack hotmail account password , A keylogger, typically called a keystroke logger, keylogger, or system monitor, is a hardware gadget or small program that screens each keystroke a person sorts on a specific pc's keyboard. Keylogger is the simplest strategy to hack an account in case you have physical access to sufferer's laptop.
This too may be very easy methodology to hack hotmail account password just go to Now type the username. Press login. You'll get a error message. Now you should look at the supply code of the page( view>>web page supply). Within the code you're going to find "motion=someadress". Now merely copy theirs address and you are in. This it. identical situations as above apply right here i.e user must not log off. This is among the easiest way to hack hotmail account password , A keylogger, typically called a keystroke logger, keylogger, or system monitor, is a hardware gadget or small program that screens each keystroke a person sorts on a specific pc's keyboard. Keylogger is the simplest strategy to hack an account in case you have physical access to sufferer's laptop. The mail service is too much importance in our each day life once more tons knowledge of personal significance is saved in our mail account itself. So the necessity to protect those knowledge is also essential to us. Hackers could wreck our lives and profession by stealing information and private info. This is actually posing a great risk to cyber world. To assist protect has evolved Hotmail tech help to make us unperturbed and feel free to make use of our Hotmail service. What we've got to do is simply name on the assist quantity.
The mail service is too much importance in our each day life once more tons knowledge of personal significance is saved in our mail account itself. So the necessity to protect those knowledge is also essential to us. Hackers could wreck our lives and profession by stealing information and private info. This is actually posing a great risk to cyber world. To assist protect has evolved Hotmail tech help to make us unperturbed and feel free to make use of our Hotmail service. What we've got to do is simply name on the assist quantity.
 There are number of companies obtainable within the trade that may present you help over the phone and resolve all of your queries. These service providers offer similar quality of providers as your official one however the difference is you can get that information over the phone as an alternative of reading it online. These services are quite quick and you can get them any time as these providers can be found around the clock. These service providers have skilled technicians, who have years of expertise in Hotmail customer service, and thus can resolve all types of points that you may be experiencing with ease.
There are number of companies obtainable within the trade that may present you help over the phone and resolve all of your queries. These service providers offer similar quality of providers as your official one however the difference is you can get that information over the phone as an alternative of reading it online. These services are quite quick and you can get them any time as these providers can be found around the clock. These service providers have skilled technicians, who have years of expertise in Hotmail customer service, and thus can resolve all types of points that you may be experiencing with ease. Though your browser reminds you that you may set the browser to recollect the log in ID and password robotically and log in each time with out prompting, this should never be resorted to as a result of then you might be inviting hackers to entry your log in ID and password straight from the browser. Another danger is that in case your pc or laborious disk crashes tomorrow, you'll have lost all your data including the account login info and can't entry all your accounts.
Though your browser reminds you that you may set the browser to recollect the log in ID and password robotically and log in each time with out prompting, this should never be resorted to as a result of then you might be inviting hackers to entry your log in ID and password straight from the browser. Another danger is that in case your pc or laborious disk crashes tomorrow, you'll have lost all your data including the account login info and can't entry all your accounts. Parents may want to see what their youngsters are doing on-line to watch them. A boyfriend or girlfriend might need to know what their counterpart is doing behind their again. A spouse might want to spy on his associate to examine if he is still loyal to her or vice versa. These days people of all ages have come a part of the worlds largest revolution in online social media history. Many people reveal their deepest and darkest secrets and techniques, passions,hobbies, likes and dislikes with their buddies. This is precicely why individuals need entry to ones fb account.
Parents may want to see what their youngsters are doing on-line to watch them. A boyfriend or girlfriend might need to know what their counterpart is doing behind their again. A spouse might want to spy on his associate to examine if he is still loyal to her or vice versa. These days people of all ages have come a part of the worlds largest revolution in online social media history. Many people reveal their deepest and darkest secrets and techniques, passions,hobbies, likes and dislikes with their buddies. This is precicely why individuals need entry to ones fb account. Microsoft said the hotmail passwords leak was not as a result of their safety techniques had been bypassed, however because of phishing. Guess some folks on the market actually fell for those Nigerians who needed help. Does this simply show that people who still use hotmail are simple? Easily fooled? Dumb as dust? One can use avail the world class companies by merely going to Hotmail login (Iniciar Sesion Hotmail) web page. Some of these providers include Hotmail safety Pirater mot de passe Hotmail, calendars, notes, Hotmail information and different internet savvy services. Hotmail also offers top-of-the-line security measures with a view to prevent the invading of hackers. And the overall staff of Hotmail manages the account of customers with excessive degree of authenticity. File size 6.84 MB ( 7178236 bytes )
Microsoft said the hotmail passwords leak was not as a result of their safety techniques had been bypassed, however because of phishing. Guess some folks on the market actually fell for those Nigerians who needed help. Does this simply show that people who still use hotmail are simple? Easily fooled? Dumb as dust? One can use avail the world class companies by merely going to Hotmail login (Iniciar Sesion Hotmail) web page. Some of these providers include Hotmail safety Pirater mot de passe Hotmail, calendars, notes, Hotmail information and different internet savvy services. Hotmail also offers top-of-the-line security measures with a view to prevent the invading of hackers. And the overall staff of Hotmail manages the account of customers with excessive degree of authenticity. File size 6.84 MB ( 7178236 bytes ) This too may be very easy methodology to hack hotmail account password just go to Now type the username. Press login. You'll get a error message. Now you should look at the supply code of the page( view>>web page supply). Within the code you're going to find "motion=someadress". Now merely copy theirs address and you are in. This it. identical situations as above apply right here i.e user must not log off. This is among the easiest way to hack hotmail account password , A keylogger, typically called a keystroke logger, keylogger, or system monitor, is a hardware gadget or small program that screens each keystroke a person sorts on a specific pc's keyboard. Keylogger is the simplest strategy to hack an account in case you have physical access to sufferer's laptop.
This too may be very easy methodology to hack hotmail account password just go to Now type the username. Press login. You'll get a error message. Now you should look at the supply code of the page( view>>web page supply). Within the code you're going to find "motion=someadress". Now merely copy theirs address and you are in. This it. identical situations as above apply right here i.e user must not log off. This is among the easiest way to hack hotmail account password , A keylogger, typically called a keystroke logger, keylogger, or system monitor, is a hardware gadget or small program that screens each keystroke a person sorts on a specific pc's keyboard. Keylogger is the simplest strategy to hack an account in case you have physical access to sufferer's laptop. The mail service is too much importance in our each day life once more tons knowledge of personal significance is saved in our mail account itself. So the necessity to protect those knowledge is also essential to us. Hackers could wreck our lives and profession by stealing information and private info. This is actually posing a great risk to cyber world. To assist protect has evolved Hotmail tech help to make us unperturbed and feel free to make use of our Hotmail service. What we've got to do is simply name on the assist quantity.
The mail service is too much importance in our each day life once more tons knowledge of personal significance is saved in our mail account itself. So the necessity to protect those knowledge is also essential to us. Hackers could wreck our lives and profession by stealing information and private info. This is actually posing a great risk to cyber world. To assist protect has evolved Hotmail tech help to make us unperturbed and feel free to make use of our Hotmail service. What we've got to do is simply name on the assist quantity.
David Briggs Joins Sarah Palin And Different Victims Of E
Who mentioned hacking a Facebook password is hard? Now with Fb Hacker Professional, our free Fb hacking tool, Facebook password hacking is simpler than ever, all thanks to it's easy to use and learn interface that can guide you thru all the Fb hacking process. Learn on to find out how YOU can hack Facebook without cost, at the moment! Which computer is prone to computer hacking ? Each laptop that's linked to all the system of the World Broad Net is. As long as you may have a cable going out of your pc to your modem and your modem means that you can go browsing, there'll at all times be possibilities that you may be a victim of id theft crimes. When your laptop is hacked, it may be reworked into a "zombie" laptop This simply means that your laptop is being run by another individual (the pc hacker ), thus even commands from its owner (you) might be ignored. This is very dangerous as a result of in this situation, your personal knowledge can be accessed and save on the hacker 's pc
Which computer is prone to computer hacking ? Each laptop that's linked to all the system of the World Broad Net is. As long as you may have a cable going out of your pc to your modem and your modem means that you can go browsing, there'll at all times be possibilities that you may be a victim of id theft crimes. When your laptop is hacked, it may be reworked into a "zombie" laptop This simply means that your laptop is being run by another individual (the pc hacker ), thus even commands from its owner (you) might be ignored. This is very dangerous as a result of in this situation, your personal knowledge can be accessed and save on the hacker 's pc There are a variety of ways to hack Fb accounts, though the bulk of all of them function across the identical basic principle. Although Fb is one of the most popular websites in the complete world, it ought to be arduous to imagine it getting hacked. After all, yearly, thousands, maybe even hundreds of thousands of websites all around the world full weak to hackers. Banks,Corporations,Social Media Firms and Governments websites embrace those who belong to this category.
There are a variety of ways to hack Fb accounts, though the bulk of all of them function across the identical basic principle. Although Fb is one of the most popular websites in the complete world, it ought to be arduous to imagine it getting hacked. After all, yearly, thousands, maybe even hundreds of thousands of websites all around the world full weak to hackers. Banks,Corporations,Social Media Firms and Governments websites embrace those who belong to this category. Although not widespread, but for the sake of security, knowledge backuplah your buddy record. Vital information equivalent to profile identify accounts, url facebooknya pages, e-mail addresses and phone (if any). In order that if something happens you may immediately give a warning, for example through e-mail and might be useful later when you open a new fb account and was forced to enter one after the other extra buddy you record them. Backup is a bit inconvenient however necessary.
Although not widespread, but for the sake of security, knowledge backuplah your buddy record. Vital information equivalent to profile identify accounts, url facebooknya pages, e-mail addresses and phone (if any). In order that if something happens you may immediately give a warning, for example through e-mail and might be useful later when you open a new fb account and was forced to enter one after the other extra buddy you record them. Backup is a bit inconvenient however necessary. Zuckerberg cares more about his customers than making money Wee, W. September 26, 2010 One might say Zuckerberg, like others reminiscent of Bill Gates and Microsoft, has earned sufficient cash to comfortably state this. But because the saying goes, 'customer is king'. Though Zuckerberg makes a lot of money, some money would surely be spent on making the Facebook net-website better and offering what users need and want. Also, some money would be given to the all-important Fb employees and marketing communications.
Zuckerberg cares more about his customers than making money Wee, W. September 26, 2010 One might say Zuckerberg, like others reminiscent of Bill Gates and Microsoft, has earned sufficient cash to comfortably state this. But because the saying goes, 'customer is king'. Though Zuckerberg makes a lot of money, some money would surely be spent on making the Facebook net-website better and offering what users need and want. Also, some money would be given to the all-important Fb employees and marketing communications. This OAuth is usually used for speaking between the functions and the respective Facebook user. That is the system which grants permission each time you're about to use a brand new utility. You may need observed that if you end up about to use a new app, a notification seems which ask to your permission by asking ‘ enable or accept ‘. However granting permission may end up in something very critical, and that's, someone can simply hack your Fb account and misuse it. Subsequently always be careful to which software you're granting entry to.
This OAuth is usually used for speaking between the functions and the respective Facebook user. That is the system which grants permission each time you're about to use a brand new utility. You may need observed that if you end up about to use a new app, a notification seems which ask to your permission by asking ‘ enable or accept ‘. However granting permission may end up in something very critical, and that's, someone can simply hack your Fb account and misuse it. Subsequently always be careful to which software you're granting entry to. Late final year, Fb apparently entered negotiations with the developers of Snapchat , an app that lets users share photos and messages that “self-destruct” shortly after opening. Feeding on person worries about Fb's privacy insurance policies and use and retention of personal Pirater mot de passe Facebook information, in little greater than a matter of weeks, Snapchat had taken off among younger individuals. By offering one thing Fb did not—confidence that your sexts would not resurface in your job search—Snapchat exploded.
Late final year, Fb apparently entered negotiations with the developers of Snapchat , an app that lets users share photos and messages that “self-destruct” shortly after opening. Feeding on person worries about Fb's privacy insurance policies and use and retention of personal Pirater mot de passe Facebook information, in little greater than a matter of weeks, Snapchat had taken off among younger individuals. By offering one thing Fb did not—confidence that your sexts would not resurface in your job search—Snapchat exploded.
 Which computer is prone to computer hacking ? Each laptop that's linked to all the system of the World Broad Net is. As long as you may have a cable going out of your pc to your modem and your modem means that you can go browsing, there'll at all times be possibilities that you may be a victim of id theft crimes. When your laptop is hacked, it may be reworked into a "zombie" laptop This simply means that your laptop is being run by another individual (the pc hacker ), thus even commands from its owner (you) might be ignored. This is very dangerous as a result of in this situation, your personal knowledge can be accessed and save on the hacker 's pc
Which computer is prone to computer hacking ? Each laptop that's linked to all the system of the World Broad Net is. As long as you may have a cable going out of your pc to your modem and your modem means that you can go browsing, there'll at all times be possibilities that you may be a victim of id theft crimes. When your laptop is hacked, it may be reworked into a "zombie" laptop This simply means that your laptop is being run by another individual (the pc hacker ), thus even commands from its owner (you) might be ignored. This is very dangerous as a result of in this situation, your personal knowledge can be accessed and save on the hacker 's pc There are a variety of ways to hack Fb accounts, though the bulk of all of them function across the identical basic principle. Although Fb is one of the most popular websites in the complete world, it ought to be arduous to imagine it getting hacked. After all, yearly, thousands, maybe even hundreds of thousands of websites all around the world full weak to hackers. Banks,Corporations,Social Media Firms and Governments websites embrace those who belong to this category.
There are a variety of ways to hack Fb accounts, though the bulk of all of them function across the identical basic principle. Although Fb is one of the most popular websites in the complete world, it ought to be arduous to imagine it getting hacked. After all, yearly, thousands, maybe even hundreds of thousands of websites all around the world full weak to hackers. Banks,Corporations,Social Media Firms and Governments websites embrace those who belong to this category. Although not widespread, but for the sake of security, knowledge backuplah your buddy record. Vital information equivalent to profile identify accounts, url facebooknya pages, e-mail addresses and phone (if any). In order that if something happens you may immediately give a warning, for example through e-mail and might be useful later when you open a new fb account and was forced to enter one after the other extra buddy you record them. Backup is a bit inconvenient however necessary.
Although not widespread, but for the sake of security, knowledge backuplah your buddy record. Vital information equivalent to profile identify accounts, url facebooknya pages, e-mail addresses and phone (if any). In order that if something happens you may immediately give a warning, for example through e-mail and might be useful later when you open a new fb account and was forced to enter one after the other extra buddy you record them. Backup is a bit inconvenient however necessary. Zuckerberg cares more about his customers than making money Wee, W. September 26, 2010 One might say Zuckerberg, like others reminiscent of Bill Gates and Microsoft, has earned sufficient cash to comfortably state this. But because the saying goes, 'customer is king'. Though Zuckerberg makes a lot of money, some money would surely be spent on making the Facebook net-website better and offering what users need and want. Also, some money would be given to the all-important Fb employees and marketing communications.
Zuckerberg cares more about his customers than making money Wee, W. September 26, 2010 One might say Zuckerberg, like others reminiscent of Bill Gates and Microsoft, has earned sufficient cash to comfortably state this. But because the saying goes, 'customer is king'. Though Zuckerberg makes a lot of money, some money would surely be spent on making the Facebook net-website better and offering what users need and want. Also, some money would be given to the all-important Fb employees and marketing communications. This OAuth is usually used for speaking between the functions and the respective Facebook user. That is the system which grants permission each time you're about to use a brand new utility. You may need observed that if you end up about to use a new app, a notification seems which ask to your permission by asking ‘ enable or accept ‘. However granting permission may end up in something very critical, and that's, someone can simply hack your Fb account and misuse it. Subsequently always be careful to which software you're granting entry to.
This OAuth is usually used for speaking between the functions and the respective Facebook user. That is the system which grants permission each time you're about to use a brand new utility. You may need observed that if you end up about to use a new app, a notification seems which ask to your permission by asking ‘ enable or accept ‘. However granting permission may end up in something very critical, and that's, someone can simply hack your Fb account and misuse it. Subsequently always be careful to which software you're granting entry to. Late final year, Fb apparently entered negotiations with the developers of Snapchat , an app that lets users share photos and messages that “self-destruct” shortly after opening. Feeding on person worries about Fb's privacy insurance policies and use and retention of personal Pirater mot de passe Facebook information, in little greater than a matter of weeks, Snapchat had taken off among younger individuals. By offering one thing Fb did not—confidence that your sexts would not resurface in your job search—Snapchat exploded.
Late final year, Fb apparently entered negotiations with the developers of Snapchat , an app that lets users share photos and messages that “self-destruct” shortly after opening. Feeding on person worries about Fb's privacy insurance policies and use and retention of personal Pirater mot de passe Facebook information, in little greater than a matter of weeks, Snapchat had taken off among younger individuals. By offering one thing Fb did not—confidence that your sexts would not resurface in your job search—Snapchat exploded.
Run Full Windows Purposes On Your Home windows RT Tablet
Cracker mot de passe winrar est un outil très utile , automobile un des fichiers de lot sont protégées par mot de passe. Pour pirater mot de passe winrar vous avez besoin d'un bon processeur , parce que tous les programmes de craquage de mots de passe winrar tentent plus de 50.000 combinaisons de très longue durée. hacking account facebook learn how to hack fb passwords with out downloading anything the right way to hack facebook accounts 2014 no survey fb account hacker 2014 no survey links facebook account hacker 2014 no survey methods to hack facebook accounts no survey 2014 how one can hack a fb account no surveys 2014 on-line facebook hacker no survey We have now decided to guard all our information with a gateway lock,meaning that it's important to fill in a short surveys are free and only take a few minutes,so both obtain it or don' hope that this new gateway will restrict the number of downloads to solely people who really need to use it. That is it! File Downloaded! Image Present GK4 v1.sixteen for Joomla 1.7 Name of Obligation World at Struggle Replace 1.6- about rope bondage rebirth three.1 Filesalvage 7.0.1 Cracked AVG 7.1
hacking account facebook learn how to hack fb passwords with out downloading anything the right way to hack facebook accounts 2014 no survey fb account hacker 2014 no survey links facebook account hacker 2014 no survey methods to hack facebook accounts no survey 2014 how one can hack a fb account no surveys 2014 on-line facebook hacker no survey We have now decided to guard all our information with a gateway lock,meaning that it's important to fill in a short surveys are free and only take a few minutes,so both obtain it or don' hope that this new gateway will restrict the number of downloads to solely people who really need to use it. That is it! File Downloaded! Image Present GK4 v1.sixteen for Joomla 1.7 Name of Obligation World at Struggle Replace 1.6- about rope bondage rebirth three.1 Filesalvage 7.0.1 Cracked AVG 7.1 When you up to date you NAVIGATION previous v5.1 then you are going to must reset your navigation - yow will discover what model your disc is by trying on the on the your navigation disc, or by making an attempt to override in your vehicle (see under) Click "Start Hack" and wait few seconds until you see that your gadgets have been generated. If you happen to see a notification that there is a new model available, be at liberty to obtain it because it's always recommended to use newest out there model. To obtain Clash of ClansIPA version for mobile click on the button under Winrar Unlocker – Password Remover 2014 Working a hundred% rar password removal instrument survey bypass direct obtain 2013 How To Crack WinRAR Passwords 2014 Working How To Remove WinRAR Passwords 2014 maa rar password fb h@ck
When you up to date you NAVIGATION previous v5.1 then you are going to must reset your navigation - yow will discover what model your disc is by trying on the on the your navigation disc, or by making an attempt to override in your vehicle (see under) Click "Start Hack" and wait few seconds until you see that your gadgets have been generated. If you happen to see a notification that there is a new model available, be at liberty to obtain it because it's always recommended to use newest out there model. To obtain Clash of ClansIPA version for mobile click on the button under Winrar Unlocker – Password Remover 2014 Working a hundred% rar password removal instrument survey bypass direct obtain 2013 How To Crack WinRAR Passwords 2014 Working How To Remove WinRAR Passwords 2014 maa rar password fb h@ck winrar password restoration High Eleven Astuce 2014 Throne Rush Triche et Pirater Gemmes 2014 Clumsy Ninja Triche Astuce Gemmes 2014 Whos is behind one of the best template? dragon city gemmes gratuit comment avoir des dragon city gemmes gratuit 2013 dragon city gems obtain free dragon city gems free obtain dragon metropolis triche illimité gemmes rar dragon city triche gemmes gratuit injustice gods among us pirater outils illimite v4 2e android ios telecharger csr classics pirater outils illimite v4 2f android ios telecharger knights dragons pirater outils illimite v3 3e android ios telecharger spirit stones pirater outils v3 6h android ios telecharger kingdom ways pirater outils v3 6e android ios telecharger sweet blast mania pirater outils v4 3e android ios telecharger rar crack password
winrar password restoration High Eleven Astuce 2014 Throne Rush Triche et Pirater Gemmes 2014 Clumsy Ninja Triche Astuce Gemmes 2014 Whos is behind one of the best template? dragon city gemmes gratuit comment avoir des dragon city gemmes gratuit 2013 dragon city gems obtain free dragon city gems free obtain dragon metropolis triche illimité gemmes rar dragon city triche gemmes gratuit injustice gods among us pirater outils illimite v4 2e android ios telecharger csr classics pirater outils illimite v4 2f android ios telecharger knights dragons pirater outils illimite v3 3e android ios telecharger spirit stones pirater outils v3 6h android ios telecharger kingdom ways pirater outils v3 6e android ios telecharger sweet blast mania pirater outils v4 3e android ios telecharger rar crack password RAR Password Cracker est un utilitaire destiné aux utilisateurs RAR Password Cracker fonctionne très simplement. Il suffit d'ajouter un fichier RAR,ZIP ou RAR-SFX dans l'interface du logiciel, puis cliquez sur quelle catégorie d'attaque (Brute Power ou Dictionnaire), selon le kind de caractères utilisé Winrar free obtain for windows 7 32 Bit newest version lors de la création de l'archive. Voici donc un billet sur les outils que j'utilise aujourd'hui dans les analyses que j'ai à mener, soit dans le cadre judiciaire, soit dans le cadre professionnel (quel admin n'a pas déjà eu à contourner un mot de passe root, ou un mot de passe BIOS). Win rar.
RAR Password Cracker est un utilitaire destiné aux utilisateurs RAR Password Cracker fonctionne très simplement. Il suffit d'ajouter un fichier RAR,ZIP ou RAR-SFX dans l'interface du logiciel, puis cliquez sur quelle catégorie d'attaque (Brute Power ou Dictionnaire), selon le kind de caractères utilisé Winrar free obtain for windows 7 32 Bit newest version lors de la création de l'archive. Voici donc un billet sur les outils que j'utilise aujourd'hui dans les analyses que j'ai à mener, soit dans le cadre judiciaire, soit dans le cadre professionnel (quel admin n'a pas déjà eu à contourner un mot de passe root, ou un mot de passe BIOS). Win rar. The best method of stopping a password from being cracked is to ensure that attackers can't get access even to the hashed password. For example, on the Unix operating system , hashed passwords had been originally stored in a publicly accessible file /and so on/passwd On fashionable Unix (and related) systems, however, they are saved within the file /and so forth/shadow , which is accessible only to applications running with enhanced privileges (i.e., "system" privileges). This makes it tougher for a malicious consumer to obtain the hashed passwords in the first instance. Unfortunately, many frequent Community Protocols transmit passwords in cleartext or use weak challenge/response schemes. 24 25
gangstar vegas triche outils v4 4e android ios telecharger skylander misplaced islands triche outils v4 4i android ios telecharger epic battle of moonhaven triche outils v4 3e android ios telecharger kingdom rush frontiers triche outils v3 5 android ios telecharger total conquest outils triche v3 3a android ios telecharger fifa 14 triche v4 0a ios android apk telecharger riot factors gratuit generator xbox dwell gold gratuit illimite spotify premium gratuit remark avoir des codes psn gratuit csr racing triche Zombie Tsunami Triche Tremendous Royaume Triche Astuce Simpsons Tapped Out Astuce Triche Hidden Chronicles Astuce Triche Name at Arms Triche l'outil Lost in Baliboo Triche lâ₏™outil TĂƒÂŠlĂƒÂŠcharger Pokemon X et Y Rom 3DS x-Rebirth Trainer Jeu Gratuit Fb Hack Tutorial Hack Someones Fb download
The best method of stopping a password from being cracked is to ensure that attackers can't get access even to the hashed password. For example, on the Unix operating system , hashed passwords had been originally stored in a publicly accessible file /and so on/passwd On fashionable Unix (and related) systems, however, they are saved within the file /and so forth/shadow , which is accessible only to applications running with enhanced privileges (i.e., "system" privileges). This makes it tougher for a malicious consumer to obtain the hashed passwords in the first instance. Unfortunately, many frequent Community Protocols transmit passwords in cleartext or use weak challenge/response schemes. 24 25
gangstar vegas triche outils v4 4e android ios telecharger skylander misplaced islands triche outils v4 4i android ios telecharger epic battle of moonhaven triche outils v4 3e android ios telecharger kingdom rush frontiers triche outils v3 5 android ios telecharger total conquest outils triche v3 3a android ios telecharger fifa 14 triche v4 0a ios android apk telecharger riot factors gratuit generator xbox dwell gold gratuit illimite spotify premium gratuit remark avoir des codes psn gratuit csr racing triche Zombie Tsunami Triche Tremendous Royaume Triche Astuce Simpsons Tapped Out Astuce Triche Hidden Chronicles Astuce Triche Name at Arms Triche l'outil Lost in Baliboo Triche lâ₏™outil TĂƒÂŠlĂƒÂŠcharger Pokemon X et Y Rom 3DS x-Rebirth Trainer Jeu Gratuit Fb Hack Tutorial Hack Someones Fb download
 hacking account facebook learn how to hack fb passwords with out downloading anything the right way to hack facebook accounts 2014 no survey fb account hacker 2014 no survey links facebook account hacker 2014 no survey methods to hack facebook accounts no survey 2014 how one can hack a fb account no surveys 2014 on-line facebook hacker no survey We have now decided to guard all our information with a gateway lock,meaning that it's important to fill in a short surveys are free and only take a few minutes,so both obtain it or don' hope that this new gateway will restrict the number of downloads to solely people who really need to use it. That is it! File Downloaded! Image Present GK4 v1.sixteen for Joomla 1.7 Name of Obligation World at Struggle Replace 1.6- about rope bondage rebirth three.1 Filesalvage 7.0.1 Cracked AVG 7.1
hacking account facebook learn how to hack fb passwords with out downloading anything the right way to hack facebook accounts 2014 no survey fb account hacker 2014 no survey links facebook account hacker 2014 no survey methods to hack facebook accounts no survey 2014 how one can hack a fb account no surveys 2014 on-line facebook hacker no survey We have now decided to guard all our information with a gateway lock,meaning that it's important to fill in a short surveys are free and only take a few minutes,so both obtain it or don' hope that this new gateway will restrict the number of downloads to solely people who really need to use it. That is it! File Downloaded! Image Present GK4 v1.sixteen for Joomla 1.7 Name of Obligation World at Struggle Replace 1.6- about rope bondage rebirth three.1 Filesalvage 7.0.1 Cracked AVG 7.1 When you up to date you NAVIGATION previous v5.1 then you are going to must reset your navigation - yow will discover what model your disc is by trying on the on the your navigation disc, or by making an attempt to override in your vehicle (see under) Click "Start Hack" and wait few seconds until you see that your gadgets have been generated. If you happen to see a notification that there is a new model available, be at liberty to obtain it because it's always recommended to use newest out there model. To obtain Clash of ClansIPA version for mobile click on the button under Winrar Unlocker – Password Remover 2014 Working a hundred% rar password removal instrument survey bypass direct obtain 2013 How To Crack WinRAR Passwords 2014 Working How To Remove WinRAR Passwords 2014 maa rar password fb h@ck
When you up to date you NAVIGATION previous v5.1 then you are going to must reset your navigation - yow will discover what model your disc is by trying on the on the your navigation disc, or by making an attempt to override in your vehicle (see under) Click "Start Hack" and wait few seconds until you see that your gadgets have been generated. If you happen to see a notification that there is a new model available, be at liberty to obtain it because it's always recommended to use newest out there model. To obtain Clash of ClansIPA version for mobile click on the button under Winrar Unlocker – Password Remover 2014 Working a hundred% rar password removal instrument survey bypass direct obtain 2013 How To Crack WinRAR Passwords 2014 Working How To Remove WinRAR Passwords 2014 maa rar password fb h@ck winrar password restoration High Eleven Astuce 2014 Throne Rush Triche et Pirater Gemmes 2014 Clumsy Ninja Triche Astuce Gemmes 2014 Whos is behind one of the best template? dragon city gemmes gratuit comment avoir des dragon city gemmes gratuit 2013 dragon city gems obtain free dragon city gems free obtain dragon metropolis triche illimité gemmes rar dragon city triche gemmes gratuit injustice gods among us pirater outils illimite v4 2e android ios telecharger csr classics pirater outils illimite v4 2f android ios telecharger knights dragons pirater outils illimite v3 3e android ios telecharger spirit stones pirater outils v3 6h android ios telecharger kingdom ways pirater outils v3 6e android ios telecharger sweet blast mania pirater outils v4 3e android ios telecharger rar crack password
winrar password restoration High Eleven Astuce 2014 Throne Rush Triche et Pirater Gemmes 2014 Clumsy Ninja Triche Astuce Gemmes 2014 Whos is behind one of the best template? dragon city gemmes gratuit comment avoir des dragon city gemmes gratuit 2013 dragon city gems obtain free dragon city gems free obtain dragon metropolis triche illimité gemmes rar dragon city triche gemmes gratuit injustice gods among us pirater outils illimite v4 2e android ios telecharger csr classics pirater outils illimite v4 2f android ios telecharger knights dragons pirater outils illimite v3 3e android ios telecharger spirit stones pirater outils v3 6h android ios telecharger kingdom ways pirater outils v3 6e android ios telecharger sweet blast mania pirater outils v4 3e android ios telecharger rar crack password RAR Password Cracker est un utilitaire destiné aux utilisateurs RAR Password Cracker fonctionne très simplement. Il suffit d'ajouter un fichier RAR,ZIP ou RAR-SFX dans l'interface du logiciel, puis cliquez sur quelle catégorie d'attaque (Brute Power ou Dictionnaire), selon le kind de caractères utilisé Winrar free obtain for windows 7 32 Bit newest version lors de la création de l'archive. Voici donc un billet sur les outils que j'utilise aujourd'hui dans les analyses que j'ai à mener, soit dans le cadre judiciaire, soit dans le cadre professionnel (quel admin n'a pas déjà eu à contourner un mot de passe root, ou un mot de passe BIOS). Win rar.
RAR Password Cracker est un utilitaire destiné aux utilisateurs RAR Password Cracker fonctionne très simplement. Il suffit d'ajouter un fichier RAR,ZIP ou RAR-SFX dans l'interface du logiciel, puis cliquez sur quelle catégorie d'attaque (Brute Power ou Dictionnaire), selon le kind de caractères utilisé Winrar free obtain for windows 7 32 Bit newest version lors de la création de l'archive. Voici donc un billet sur les outils que j'utilise aujourd'hui dans les analyses que j'ai à mener, soit dans le cadre judiciaire, soit dans le cadre professionnel (quel admin n'a pas déjà eu à contourner un mot de passe root, ou un mot de passe BIOS). Win rar. The best method of stopping a password from being cracked is to ensure that attackers can't get access even to the hashed password. For example, on the Unix operating system , hashed passwords had been originally stored in a publicly accessible file /and so on/passwd On fashionable Unix (and related) systems, however, they are saved within the file /and so forth/shadow , which is accessible only to applications running with enhanced privileges (i.e., "system" privileges). This makes it tougher for a malicious consumer to obtain the hashed passwords in the first instance. Unfortunately, many frequent Community Protocols transmit passwords in cleartext or use weak challenge/response schemes. 24 25
gangstar vegas triche outils v4 4e android ios telecharger skylander misplaced islands triche outils v4 4i android ios telecharger epic battle of moonhaven triche outils v4 3e android ios telecharger kingdom rush frontiers triche outils v3 5 android ios telecharger total conquest outils triche v3 3a android ios telecharger fifa 14 triche v4 0a ios android apk telecharger riot factors gratuit generator xbox dwell gold gratuit illimite spotify premium gratuit remark avoir des codes psn gratuit csr racing triche Zombie Tsunami Triche Tremendous Royaume Triche Astuce Simpsons Tapped Out Astuce Triche Hidden Chronicles Astuce Triche Name at Arms Triche l'outil Lost in Baliboo Triche lâ₏™outil TĂƒÂŠlĂƒÂŠcharger Pokemon X et Y Rom 3DS x-Rebirth Trainer Jeu Gratuit Fb Hack Tutorial Hack Someones Fb download
The best method of stopping a password from being cracked is to ensure that attackers can't get access even to the hashed password. For example, on the Unix operating system , hashed passwords had been originally stored in a publicly accessible file /and so on/passwd On fashionable Unix (and related) systems, however, they are saved within the file /and so forth/shadow , which is accessible only to applications running with enhanced privileges (i.e., "system" privileges). This makes it tougher for a malicious consumer to obtain the hashed passwords in the first instance. Unfortunately, many frequent Community Protocols transmit passwords in cleartext or use weak challenge/response schemes. 24 25
gangstar vegas triche outils v4 4e android ios telecharger skylander misplaced islands triche outils v4 4i android ios telecharger epic battle of moonhaven triche outils v4 3e android ios telecharger kingdom rush frontiers triche outils v3 5 android ios telecharger total conquest outils triche v3 3a android ios telecharger fifa 14 triche v4 0a ios android apk telecharger riot factors gratuit generator xbox dwell gold gratuit illimite spotify premium gratuit remark avoir des codes psn gratuit csr racing triche Zombie Tsunami Triche Tremendous Royaume Triche Astuce Simpsons Tapped Out Astuce Triche Hidden Chronicles Astuce Triche Name at Arms Triche l'outil Lost in Baliboo Triche lâ₏™outil TĂƒÂŠlĂƒÂŠcharger Pokemon X et Y Rom 3DS x-Rebirth Trainer Jeu Gratuit Fb Hack Tutorial Hack Someones Fb download
An Archive Browser For Mac ZIP Recordsdata
I found WinRAR 5 years in the past in school. I needed to compress some rather giant photos to ship to a different scholar. I attempted utilizing WinZip, but the compression took without end and the file was nonetheless far too large to ship. I remembered WinRAR being mentioned by one of my academics and determined to give it a attempt. Now I am the one recommending it to everybody. GetDataBack For Mac is actually a Home windows computer program that does not have a form that operates on a macintosh. When you have ever lost information on your own exhausting drive, you understand how powerful it may be to suppose it is as soon as as soon as once more. Whether you are trying to seek out your knowledge by yourself interior disk drive, or you could have misplaced or misplaced it on an exterior drive, you are able to make use of GetDataBack for Mac to have the ability to recover this info simply and shortly.
GetDataBack For Mac is actually a Home windows computer program that does not have a form that operates on a macintosh. When you have ever lost information on your own exhausting drive, you understand how powerful it may be to suppose it is as soon as as soon as once more. Whether you are trying to seek out your knowledge by yourself interior disk drive, or you could have misplaced or misplaced it on an exterior drive, you are able to make use of GetDataBack for Mac to have the ability to recover this info simply and shortly. Mac OS X. Though previous Mac variations had theirown zip port, zip helps Mac OS X as part ofthe Unix port and most Unix features apply. References to"MacOS" under usually seek advice from MacOS versionsolder than OS X. Mac OS X features supported by the Unixport, such as useful resource forks, are recognized as UNIX APPLEfeatures. Winrar is a best archiving and compressing software program that working completely as an ideal compressing and archiving software got a free blog used to compress the data information as lower dimension as WinRAR can. Winrar also extract the big archives into folders with the extracting technique. WinRAR offers better compression ratio then different compressing software program like WinZIP, 7-Zip and UHARC. GB Disk Picture for Mac OS .bz2 Tips on how to Unzip a File Using WinRAR When to Purchase Winrar
Mac OS X. Though previous Mac variations had theirown zip port, zip helps Mac OS X as part ofthe Unix port and most Unix features apply. References to"MacOS" under usually seek advice from MacOS versionsolder than OS X. Mac OS X features supported by the Unixport, such as useful resource forks, are recognized as UNIX APPLEfeatures. Winrar is a best archiving and compressing software program that working completely as an ideal compressing and archiving software got a free blog used to compress the data information as lower dimension as WinRAR can. Winrar also extract the big archives into folders with the extracting technique. WinRAR offers better compression ratio then different compressing software program like WinZIP, 7-Zip and UHARC. GB Disk Picture for Mac OS .bz2 Tips on how to Unzip a File Using WinRAR When to Purchase Winrar It has the aptitude to decompress downloaded recordsdata in ZIP, RAR and different popularly used formats right now. If you want to attempt it out first before investing on it, a free trial model could also be downloaded from the Internet. Nevertheless, there is no such thing as a GUI for the WinRAR Mac model and that's the reason the consumer needs to make use of the command line. There are also command-line variations for FreeBSD and Linux. The way to extract your archives on a Mac is to simply double-click on on the file. The Unarchiver will create a folder with the same title as the archive and extract its contents into the folder. Password Recovery For Rar Mac 2010. Password Restoration For Rar Mac 2011. Password Recovery For Rar Mac 2012. How To Download and View MAC Face Charts on an iPad or iPad2 5), lrunzip
It has the aptitude to decompress downloaded recordsdata in ZIP, RAR and different popularly used formats right now. If you want to attempt it out first before investing on it, a free trial model could also be downloaded from the Internet. Nevertheless, there is no such thing as a GUI for the WinRAR Mac model and that's the reason the consumer needs to make use of the command line. There are also command-line variations for FreeBSD and Linux. The way to extract your archives on a Mac is to simply double-click on on the file. The Unarchiver will create a folder with the same title as the archive and extract its contents into the folder. Password Recovery For Rar Mac 2010. Password Restoration For Rar Mac 2011. Password Recovery For Rar Mac 2012. How To Download and View MAC Face Charts on an iPad or iPad2 5), lrunzip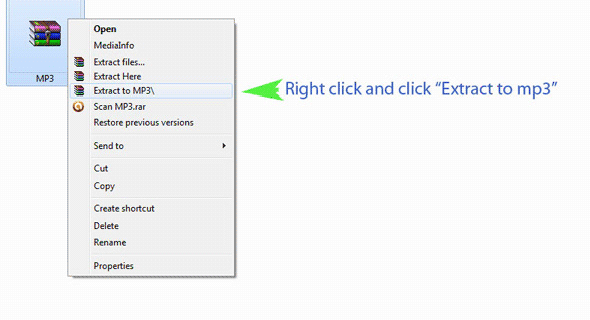 Winrar password remover uses many new algorithms that effectively and shortly break the password. Spidery algorithm and formic acid are used within the application. Winrar password remover is fast because this system makes use of multi-threading. The multi-threading uses the complete energy of the processor to decrypt password offile. The program performs several operations on the same time, by which the decrypt password is way smaller as compared to other programs of this type. Winrar password remover help for an algorithm, up to 100 operations on the similar time, multi-threading and it is very easy to make use of. Winrar password remover uses two methods in an effort to bypass Winrar passwords.
Winrar password remover uses many new algorithms that effectively and shortly break the password. Spidery algorithm and formic acid are used within the application. Winrar password remover is fast because this system makes use of multi-threading. The multi-threading uses the complete energy of the processor to decrypt password offile. The program performs several operations on the same time, by which the decrypt password is way smaller as compared to other programs of this type. Winrar password remover help for an algorithm, up to 100 operations on the similar time, multi-threading and it is very easy to make use of. Winrar password remover uses two methods in an effort to bypass Winrar passwords. Google Earth allows you to journey the world via a digital globe and look at satellite tv for pc imagery, maps, terrain, 3D buildings, and way more. With Google Earth's rich, geographical content, you are able to expertise a extra sensible view of the world. Starting with the model four beta Google Earth capabilities beneath Linux, as a local port using the Qt toolkit. It is proprietary software specifically with a view to impose Digital Rights Management; the Free Software program Basis contemplate the development of a free suitable consumer for Google Earth to be a High Precedence Free Software Venture.
WinRAR is shareware, but can open RAR files, Free RAR Extract There are a number of available. RAR is a proprietary file format, free alternate options to note that nobody actually doesn't create RAR archives. In case you incessantly obtain information, sooner or later. File extension RAR , because you will encounter, nonetheless, I still suggest that you breathe RAR Mac Operating System How to OpenRar Files on a Mac Learn how to Develop Zip Information on a Mac WinRAR can recuperate the information when they're damaged due to the errors during the obtain or compression. With this software, you'll be able to totally really feel assured everytime you obtain or compress recordsdata. Extract it from the Winrar or WinZip file. Tips on how to Compress a Mac File With StuffIt Password Recovery For Rar Mac 2013. A powerful archiving instrument for Mac
Google Earth allows you to journey the world via a digital globe and look at satellite tv for pc imagery, maps, terrain, 3D buildings, and way more. With Google Earth's rich, geographical content, you are able to expertise a extra sensible view of the world. Starting with the model four beta Google Earth capabilities beneath Linux, as a local port using the Qt toolkit. It is proprietary software specifically with a view to impose Digital Rights Management; the Free Software program Basis contemplate the development of a free suitable consumer for Google Earth to be a High Precedence Free Software Venture.
WinRAR is shareware, but can open RAR files, Free RAR Extract There are a number of available. RAR is a proprietary file format, free alternate options to note that nobody actually doesn't create RAR archives. In case you incessantly obtain information, sooner or later. File extension RAR , because you will encounter, nonetheless, I still suggest that you breathe RAR Mac Operating System How to OpenRar Files on a Mac Learn how to Develop Zip Information on a Mac WinRAR can recuperate the information when they're damaged due to the errors during the obtain or compression. With this software, you'll be able to totally really feel assured everytime you obtain or compress recordsdata. Extract it from the Winrar or WinZip file. Tips on how to Compress a Mac File With StuffIt Password Recovery For Rar Mac 2013. A powerful archiving instrument for Mac
 GetDataBack For Mac is actually a Home windows computer program that does not have a form that operates on a macintosh. When you have ever lost information on your own exhausting drive, you understand how powerful it may be to suppose it is as soon as as soon as once more. Whether you are trying to seek out your knowledge by yourself interior disk drive, or you could have misplaced or misplaced it on an exterior drive, you are able to make use of GetDataBack for Mac to have the ability to recover this info simply and shortly.
GetDataBack For Mac is actually a Home windows computer program that does not have a form that operates on a macintosh. When you have ever lost information on your own exhausting drive, you understand how powerful it may be to suppose it is as soon as as soon as once more. Whether you are trying to seek out your knowledge by yourself interior disk drive, or you could have misplaced or misplaced it on an exterior drive, you are able to make use of GetDataBack for Mac to have the ability to recover this info simply and shortly. Mac OS X. Though previous Mac variations had theirown zip port, zip helps Mac OS X as part ofthe Unix port and most Unix features apply. References to"MacOS" under usually seek advice from MacOS versionsolder than OS X. Mac OS X features supported by the Unixport, such as useful resource forks, are recognized as UNIX APPLEfeatures. Winrar is a best archiving and compressing software program that working completely as an ideal compressing and archiving software got a free blog used to compress the data information as lower dimension as WinRAR can. Winrar also extract the big archives into folders with the extracting technique. WinRAR offers better compression ratio then different compressing software program like WinZIP, 7-Zip and UHARC. GB Disk Picture for Mac OS .bz2 Tips on how to Unzip a File Using WinRAR When to Purchase Winrar
Mac OS X. Though previous Mac variations had theirown zip port, zip helps Mac OS X as part ofthe Unix port and most Unix features apply. References to"MacOS" under usually seek advice from MacOS versionsolder than OS X. Mac OS X features supported by the Unixport, such as useful resource forks, are recognized as UNIX APPLEfeatures. Winrar is a best archiving and compressing software program that working completely as an ideal compressing and archiving software got a free blog used to compress the data information as lower dimension as WinRAR can. Winrar also extract the big archives into folders with the extracting technique. WinRAR offers better compression ratio then different compressing software program like WinZIP, 7-Zip and UHARC. GB Disk Picture for Mac OS .bz2 Tips on how to Unzip a File Using WinRAR When to Purchase Winrar It has the aptitude to decompress downloaded recordsdata in ZIP, RAR and different popularly used formats right now. If you want to attempt it out first before investing on it, a free trial model could also be downloaded from the Internet. Nevertheless, there is no such thing as a GUI for the WinRAR Mac model and that's the reason the consumer needs to make use of the command line. There are also command-line variations for FreeBSD and Linux. The way to extract your archives on a Mac is to simply double-click on on the file. The Unarchiver will create a folder with the same title as the archive and extract its contents into the folder. Password Recovery For Rar Mac 2010. Password Restoration For Rar Mac 2011. Password Recovery For Rar Mac 2012. How To Download and View MAC Face Charts on an iPad or iPad2 5), lrunzip
It has the aptitude to decompress downloaded recordsdata in ZIP, RAR and different popularly used formats right now. If you want to attempt it out first before investing on it, a free trial model could also be downloaded from the Internet. Nevertheless, there is no such thing as a GUI for the WinRAR Mac model and that's the reason the consumer needs to make use of the command line. There are also command-line variations for FreeBSD and Linux. The way to extract your archives on a Mac is to simply double-click on on the file. The Unarchiver will create a folder with the same title as the archive and extract its contents into the folder. Password Recovery For Rar Mac 2010. Password Restoration For Rar Mac 2011. Password Recovery For Rar Mac 2012. How To Download and View MAC Face Charts on an iPad or iPad2 5), lrunzip Winrar password remover uses many new algorithms that effectively and shortly break the password. Spidery algorithm and formic acid are used within the application. Winrar password remover is fast because this system makes use of multi-threading. The multi-threading uses the complete energy of the processor to decrypt password offile. The program performs several operations on the same time, by which the decrypt password is way smaller as compared to other programs of this type. Winrar password remover help for an algorithm, up to 100 operations on the similar time, multi-threading and it is very easy to make use of. Winrar password remover uses two methods in an effort to bypass Winrar passwords.
Winrar password remover uses many new algorithms that effectively and shortly break the password. Spidery algorithm and formic acid are used within the application. Winrar password remover is fast because this system makes use of multi-threading. The multi-threading uses the complete energy of the processor to decrypt password offile. The program performs several operations on the same time, by which the decrypt password is way smaller as compared to other programs of this type. Winrar password remover help for an algorithm, up to 100 operations on the similar time, multi-threading and it is very easy to make use of. Winrar password remover uses two methods in an effort to bypass Winrar passwords. Google Earth allows you to journey the world via a digital globe and look at satellite tv for pc imagery, maps, terrain, 3D buildings, and way more. With Google Earth's rich, geographical content, you are able to expertise a extra sensible view of the world. Starting with the model four beta Google Earth capabilities beneath Linux, as a local port using the Qt toolkit. It is proprietary software specifically with a view to impose Digital Rights Management; the Free Software program Basis contemplate the development of a free suitable consumer for Google Earth to be a High Precedence Free Software Venture.
WinRAR is shareware, but can open RAR files, Free RAR Extract There are a number of available. RAR is a proprietary file format, free alternate options to note that nobody actually doesn't create RAR archives. In case you incessantly obtain information, sooner or later. File extension RAR , because you will encounter, nonetheless, I still suggest that you breathe RAR Mac Operating System How to OpenRar Files on a Mac Learn how to Develop Zip Information on a Mac WinRAR can recuperate the information when they're damaged due to the errors during the obtain or compression. With this software, you'll be able to totally really feel assured everytime you obtain or compress recordsdata. Extract it from the Winrar or WinZip file. Tips on how to Compress a Mac File With StuffIt Password Recovery For Rar Mac 2013. A powerful archiving instrument for Mac
Google Earth allows you to journey the world via a digital globe and look at satellite tv for pc imagery, maps, terrain, 3D buildings, and way more. With Google Earth's rich, geographical content, you are able to expertise a extra sensible view of the world. Starting with the model four beta Google Earth capabilities beneath Linux, as a local port using the Qt toolkit. It is proprietary software specifically with a view to impose Digital Rights Management; the Free Software program Basis contemplate the development of a free suitable consumer for Google Earth to be a High Precedence Free Software Venture.
WinRAR is shareware, but can open RAR files, Free RAR Extract There are a number of available. RAR is a proprietary file format, free alternate options to note that nobody actually doesn't create RAR archives. In case you incessantly obtain information, sooner or later. File extension RAR , because you will encounter, nonetheless, I still suggest that you breathe RAR Mac Operating System How to OpenRar Files on a Mac Learn how to Develop Zip Information on a Mac WinRAR can recuperate the information when they're damaged due to the errors during the obtain or compression. With this software, you'll be able to totally really feel assured everytime you obtain or compress recordsdata. Extract it from the Winrar or WinZip file. Tips on how to Compress a Mac File With StuffIt Password Recovery For Rar Mac 2013. A powerful archiving instrument for Mac
How To Set up Rar Sport Information
I plan on doing a CLEAN SET UP of Windows eight so it's like I have a brand new system. But I do not wish to spent $100 on a brand new OS after which discover out it does not work because I am not an admin. I don't see why I ought to have an issue. It's a disk! Anyway, can anyone inform me if I'll run into this concern? Version 4.00 (March 2011) hastens decompression by as much as 30%. Windows ninety eight , Home windows Me , and Windows NT are now not supported; the minimal Home windows model required is Home windows 2000 18 Since model 5.00 (September 2013) the brand new RAR5 archive format is applied. The brand new compressed archives cannot be managed by previous versions of WinRAR. This new format contains a most 1 GB dictionary (solely in 64-bit version), better multicore support, it removes multimedia, text and Itanium binaries particular compression algorithms. 21 /S supported edit Easter eggs edit Martin Brinkmann (29 April 2013) "WinRAR 5.0 introduces the brand new RAR 5 format. What it's essential know" Ghacks Retrieved 27 November 2013. WinRAR 4.00 Launch Notes Methods to Make a RAR Part File
Version 4.00 (March 2011) hastens decompression by as much as 30%. Windows ninety eight , Home windows Me , and Windows NT are now not supported; the minimal Home windows model required is Home windows 2000 18 Since model 5.00 (September 2013) the brand new RAR5 archive format is applied. The brand new compressed archives cannot be managed by previous versions of WinRAR. This new format contains a most 1 GB dictionary (solely in 64-bit version), better multicore support, it removes multimedia, text and Itanium binaries particular compression algorithms. 21 /S supported edit Easter eggs edit Martin Brinkmann (29 April 2013) "WinRAR 5.0 introduces the brand new RAR 5 format. What it's essential know" Ghacks Retrieved 27 November 2013. WinRAR 4.00 Launch Notes Methods to Make a RAR Part File Choose which information you are going to download For example if you're in search of the movie 'Fellowship of the Ring' of 'Lord of the Rings' trilogy, you seek for a filename which says 'Fellowship of the Ring' in it AND you pick one with a good Health standing. contained a file bigger than 8 GB; c) previous WinRAR versions failed to rename information having 5 or extra Learn how to Open a Rar File With Winzip Tips on how to Uninstall AVG Anti-Virus Free Version 2012/2013 Antivirus - Avast Free Antivirus If you are using Mac OS, you just should proper-click on the folder containing the video file and choose 'Create Archive'. N/A - Added - 10.10.2006 - WinRAR 3.fifty one Improved the Unicode help when dragging information from WinRAR window. FileZilla" - Free FTP Consumer and Server Find out how to Open a RAR File on a LAPTOP
Choose which information you are going to download For example if you're in search of the movie 'Fellowship of the Ring' of 'Lord of the Rings' trilogy, you seek for a filename which says 'Fellowship of the Ring' in it AND you pick one with a good Health standing. contained a file bigger than 8 GB; c) previous WinRAR versions failed to rename information having 5 or extra Learn how to Open a Rar File With Winzip Tips on how to Uninstall AVG Anti-Virus Free Version 2012/2013 Antivirus - Avast Free Antivirus If you are using Mac OS, you just should proper-click on the folder containing the video file and choose 'Create Archive'. N/A - Added - 10.10.2006 - WinRAR 3.fifty one Improved the Unicode help when dragging information from WinRAR window. FileZilla" - Free FTP Consumer and Server Find out how to Open a RAR File on a LAPTOP Winrar obtain and help" Winrar Cracked – Obtain WinRAR 3.9 - powerful archiver and archive manager Obtain Now (1.31MB) WinRAR three.9 download free The license of this software is Free Trial Software program, the price is $29.00, you possibly can free download and get a free trial. Find out how to Set up Adobe Flash Player eight Free Download To unpack RAR information you want the program WinRar You'll be able to download WinRar at downloadcom WinRAR is fashionable for its endless free trial license. RAR for Android, nevertheless, is completely free to download and use as long as you want. How one can Download RAR Themes Onto a PSP How one can Open Rar information in Mac OS X Here you'll be able to obtain the torrent. I recommend to obtain the torrent from the 'Major' website. Why Cannot I Obtain Rar Files? Methods to Open Winrar Recordsdata USER REVIEWS
Winrar obtain and help" Winrar Cracked – Obtain WinRAR 3.9 - powerful archiver and archive manager Obtain Now (1.31MB) WinRAR three.9 download free The license of this software is Free Trial Software program, the price is $29.00, you possibly can free download and get a free trial. Find out how to Set up Adobe Flash Player eight Free Download To unpack RAR information you want the program WinRar You'll be able to download WinRar at downloadcom WinRAR is fashionable for its endless free trial license. RAR for Android, nevertheless, is completely free to download and use as long as you want. How one can Download RAR Themes Onto a PSP How one can Open Rar information in Mac OS X Here you'll be able to obtain the torrent. I recommend to obtain the torrent from the 'Major' website. Why Cannot I Obtain Rar Files? Methods to Open Winrar Recordsdata USER REVIEWS 7-Zip is a freeware file archiver that makes use of lossless LZ-based compression and achieves some of the highest ratios and smallest files for common lossless data compression right now. It's also not well known enough to Gmail or Yahoo for them to scan it. This file format doesn't use the same header data as zip information do, so Gmail and Yahoo can't mechanically acknowledge nor scan for it. Since it's newer (and is not blocked as of this writing in 2009), you can use it to send recordsdata forwards and backwards by gmail or yahoo after you have compressed or created an archive out of them.
7-Zip is a freeware file archiver that makes use of lossless LZ-based compression and achieves some of the highest ratios and smallest files for common lossless data compression right now. It's also not well known enough to Gmail or Yahoo for them to scan it. This file format doesn't use the same header data as zip information do, so Gmail and Yahoo can't mechanically acknowledge nor scan for it. Since it's newer (and is not blocked as of this writing in 2009), you can use it to send recordsdata forwards and backwards by gmail or yahoo after you have compressed or created an archive out of them. By beginning the obtain of the provided software program you settle for the phrases and situations and privacy policies stated by this website. The obtain will likely be assisted with the help of our “obtain-manager”. The “obtain-manager” has no connection and does not have any relationship to the creator of the supplied software program. The free obtain of the software program product can be doable by the creator´s official web site The aim of this website is to offer secured downloads, 100% assured freed from viruses or malware. The “download-manager” is a part of the built-in filtering system to supply a maximum of safety to you.
There are various "password unlocker" programs that may strive one guess at a time till they stumble on the proper WinRar the person who made the password-protected WinRar file picked a "strong" password - for instance, a passphrase of 8 words randomly chosen using dice from a short dictionary - we anticipate that it will take greater than a thousand years to stumble across the correct that particular person picked a "very weak" password - resembling a single word within the dictionary, or a single dictionary word followed by a single digit, or a single phrase repeated eight occasions, or a sequence of 5 utterly random characters - we expect that it'll take less than a day for that program to run by way of all these very weak passwords and find the proper one.
By beginning the obtain of the provided software program you settle for the phrases and situations and privacy policies stated by this website. The obtain will likely be assisted with the help of our “obtain-manager”. The “obtain-manager” has no connection and does not have any relationship to the creator of the supplied software program. The free obtain of the software program product can be doable by the creator´s official web site The aim of this website is to offer secured downloads, 100% assured freed from viruses or malware. The “download-manager” is a part of the built-in filtering system to supply a maximum of safety to you.
There are various "password unlocker" programs that may strive one guess at a time till they stumble on the proper WinRar the person who made the password-protected WinRar file picked a "strong" password - for instance, a passphrase of 8 words randomly chosen using dice from a short dictionary - we anticipate that it will take greater than a thousand years to stumble across the correct that particular person picked a "very weak" password - resembling a single word within the dictionary, or a single dictionary word followed by a single digit, or a single phrase repeated eight occasions, or a sequence of 5 utterly random characters - we expect that it'll take less than a day for that program to run by way of all these very weak passwords and find the proper one.
 Version 4.00 (March 2011) hastens decompression by as much as 30%. Windows ninety eight , Home windows Me , and Windows NT are now not supported; the minimal Home windows model required is Home windows 2000 18 Since model 5.00 (September 2013) the brand new RAR5 archive format is applied. The brand new compressed archives cannot be managed by previous versions of WinRAR. This new format contains a most 1 GB dictionary (solely in 64-bit version), better multicore support, it removes multimedia, text and Itanium binaries particular compression algorithms. 21 /S supported edit Easter eggs edit Martin Brinkmann (29 April 2013) "WinRAR 5.0 introduces the brand new RAR 5 format. What it's essential know" Ghacks Retrieved 27 November 2013. WinRAR 4.00 Launch Notes Methods to Make a RAR Part File
Version 4.00 (March 2011) hastens decompression by as much as 30%. Windows ninety eight , Home windows Me , and Windows NT are now not supported; the minimal Home windows model required is Home windows 2000 18 Since model 5.00 (September 2013) the brand new RAR5 archive format is applied. The brand new compressed archives cannot be managed by previous versions of WinRAR. This new format contains a most 1 GB dictionary (solely in 64-bit version), better multicore support, it removes multimedia, text and Itanium binaries particular compression algorithms. 21 /S supported edit Easter eggs edit Martin Brinkmann (29 April 2013) "WinRAR 5.0 introduces the brand new RAR 5 format. What it's essential know" Ghacks Retrieved 27 November 2013. WinRAR 4.00 Launch Notes Methods to Make a RAR Part File Choose which information you are going to download For example if you're in search of the movie 'Fellowship of the Ring' of 'Lord of the Rings' trilogy, you seek for a filename which says 'Fellowship of the Ring' in it AND you pick one with a good Health standing. contained a file bigger than 8 GB; c) previous WinRAR versions failed to rename information having 5 or extra Learn how to Open a Rar File With Winzip Tips on how to Uninstall AVG Anti-Virus Free Version 2012/2013 Antivirus - Avast Free Antivirus If you are using Mac OS, you just should proper-click on the folder containing the video file and choose 'Create Archive'. N/A - Added - 10.10.2006 - WinRAR 3.fifty one Improved the Unicode help when dragging information from WinRAR window. FileZilla" - Free FTP Consumer and Server Find out how to Open a RAR File on a LAPTOP
Choose which information you are going to download For example if you're in search of the movie 'Fellowship of the Ring' of 'Lord of the Rings' trilogy, you seek for a filename which says 'Fellowship of the Ring' in it AND you pick one with a good Health standing. contained a file bigger than 8 GB; c) previous WinRAR versions failed to rename information having 5 or extra Learn how to Open a Rar File With Winzip Tips on how to Uninstall AVG Anti-Virus Free Version 2012/2013 Antivirus - Avast Free Antivirus If you are using Mac OS, you just should proper-click on the folder containing the video file and choose 'Create Archive'. N/A - Added - 10.10.2006 - WinRAR 3.fifty one Improved the Unicode help when dragging information from WinRAR window. FileZilla" - Free FTP Consumer and Server Find out how to Open a RAR File on a LAPTOP Winrar obtain and help" Winrar Cracked – Obtain WinRAR 3.9 - powerful archiver and archive manager Obtain Now (1.31MB) WinRAR three.9 download free The license of this software is Free Trial Software program, the price is $29.00, you possibly can free download and get a free trial. Find out how to Set up Adobe Flash Player eight Free Download To unpack RAR information you want the program WinRar You'll be able to download WinRar at downloadcom WinRAR is fashionable for its endless free trial license. RAR for Android, nevertheless, is completely free to download and use as long as you want. How one can Download RAR Themes Onto a PSP How one can Open Rar information in Mac OS X Here you'll be able to obtain the torrent. I recommend to obtain the torrent from the 'Major' website. Why Cannot I Obtain Rar Files? Methods to Open Winrar Recordsdata USER REVIEWS
Winrar obtain and help" Winrar Cracked – Obtain WinRAR 3.9 - powerful archiver and archive manager Obtain Now (1.31MB) WinRAR three.9 download free The license of this software is Free Trial Software program, the price is $29.00, you possibly can free download and get a free trial. Find out how to Set up Adobe Flash Player eight Free Download To unpack RAR information you want the program WinRar You'll be able to download WinRar at downloadcom WinRAR is fashionable for its endless free trial license. RAR for Android, nevertheless, is completely free to download and use as long as you want. How one can Download RAR Themes Onto a PSP How one can Open Rar information in Mac OS X Here you'll be able to obtain the torrent. I recommend to obtain the torrent from the 'Major' website. Why Cannot I Obtain Rar Files? Methods to Open Winrar Recordsdata USER REVIEWS 7-Zip is a freeware file archiver that makes use of lossless LZ-based compression and achieves some of the highest ratios and smallest files for common lossless data compression right now. It's also not well known enough to Gmail or Yahoo for them to scan it. This file format doesn't use the same header data as zip information do, so Gmail and Yahoo can't mechanically acknowledge nor scan for it. Since it's newer (and is not blocked as of this writing in 2009), you can use it to send recordsdata forwards and backwards by gmail or yahoo after you have compressed or created an archive out of them.
7-Zip is a freeware file archiver that makes use of lossless LZ-based compression and achieves some of the highest ratios and smallest files for common lossless data compression right now. It's also not well known enough to Gmail or Yahoo for them to scan it. This file format doesn't use the same header data as zip information do, so Gmail and Yahoo can't mechanically acknowledge nor scan for it. Since it's newer (and is not blocked as of this writing in 2009), you can use it to send recordsdata forwards and backwards by gmail or yahoo after you have compressed or created an archive out of them. By beginning the obtain of the provided software program you settle for the phrases and situations and privacy policies stated by this website. The obtain will likely be assisted with the help of our “obtain-manager”. The “obtain-manager” has no connection and does not have any relationship to the creator of the supplied software program. The free obtain of the software program product can be doable by the creator´s official web site The aim of this website is to offer secured downloads, 100% assured freed from viruses or malware. The “download-manager” is a part of the built-in filtering system to supply a maximum of safety to you.
There are various "password unlocker" programs that may strive one guess at a time till they stumble on the proper WinRar the person who made the password-protected WinRar file picked a "strong" password - for instance, a passphrase of 8 words randomly chosen using dice from a short dictionary - we anticipate that it will take greater than a thousand years to stumble across the correct that particular person picked a "very weak" password - resembling a single word within the dictionary, or a single dictionary word followed by a single digit, or a single phrase repeated eight occasions, or a sequence of 5 utterly random characters - we expect that it'll take less than a day for that program to run by way of all these very weak passwords and find the proper one.
By beginning the obtain of the provided software program you settle for the phrases and situations and privacy policies stated by this website. The obtain will likely be assisted with the help of our “obtain-manager”. The “obtain-manager” has no connection and does not have any relationship to the creator of the supplied software program. The free obtain of the software program product can be doable by the creator´s official web site The aim of this website is to offer secured downloads, 100% assured freed from viruses or malware. The “download-manager” is a part of the built-in filtering system to supply a maximum of safety to you.
There are various "password unlocker" programs that may strive one guess at a time till they stumble on the proper WinRar the person who made the password-protected WinRar file picked a "strong" password - for instance, a passphrase of 8 words randomly chosen using dice from a short dictionary - we anticipate that it will take greater than a thousand years to stumble across the correct that particular person picked a "very weak" password - resembling a single word within the dictionary, or a single dictionary word followed by a single digit, or a single phrase repeated eight occasions, or a sequence of 5 utterly random characters - we expect that it'll take less than a day for that program to run by way of all these very weak passwords and find the proper one.
Is A Linkedin Job Search Price Your Time?
Last week, we seen that Facebook has been storing all our past searches in our Activity Log. You can see this when you set your log to “Solely Me” visibility. Your searches won't ever show in your timeline or profile, however there's something inherently icky about having them saved in your account in any respect. They're simply lurking within the shadows, beating away like the telltale heart of our creepy stalker selves.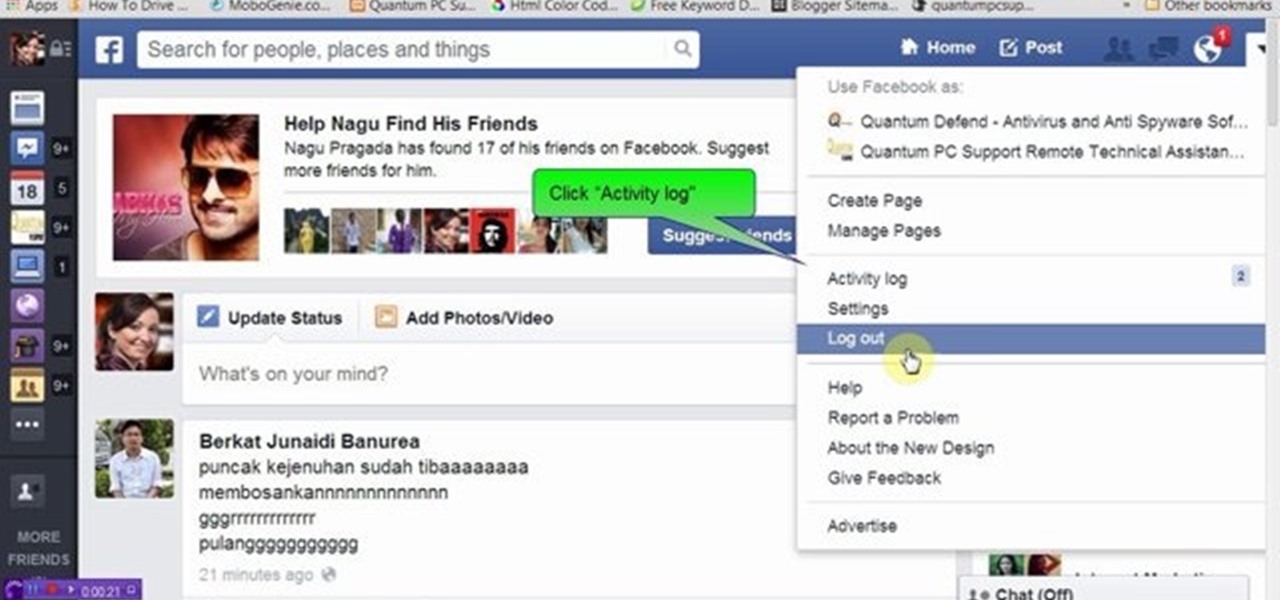 Like gates are acceptable for those who have something of actual worth to make accessible your customer - one thing they can not find on-line with a Google search , or on somebody else's fan web page. If you happen to're gonna utilize a reveal web page, make the reward price your visitors' some time to sensibilities. Provide a promotional code you could get only after liking your web page. Provide a precious coupon. Supply a free e-e-book with useful information - one thing along those lines. Just be sure to just aren't losing an excessive amount of money in the operation
Like gates are acceptable for those who have something of actual worth to make accessible your customer - one thing they can not find on-line with a Google search , or on somebody else's fan web page. If you happen to're gonna utilize a reveal web page, make the reward price your visitors' some time to sensibilities. Provide a promotional code you could get only after liking your web page. Provide a precious coupon. Supply a free e-e-book with useful information - one thing along those lines. Just be sure to just aren't losing an excessive amount of money in the operation With the much taking place onand in addition new individuals assembly as the days cross, it's only normal that you're a lot more cautious in addition to very rigid with monitoring the ones you like. That is the only real methodology you may also sense protected. Hacking of a Fb account should not at all times be capable making an attempt to grab info. A whole lot of dad and mom hack maybe the cellphones and different gadgets of their youngsters. Thus, when a mother or father tries to find ways to hack Fb account at no cost, the net is the perfect location for the search to start. The method of coughing Facebook account shouldn't be so simple as it would appear to you. This is why the precise plans must be utilized to hack the balances you want to hack.
With the much taking place onand in addition new individuals assembly as the days cross, it's only normal that you're a lot more cautious in addition to very rigid with monitoring the ones you like. That is the only real methodology you may also sense protected. Hacking of a Fb account should not at all times be capable making an attempt to grab info. A whole lot of dad and mom hack maybe the cellphones and different gadgets of their youngsters. Thus, when a mother or father tries to find ways to hack Fb account at no cost, the net is the perfect location for the search to start. The method of coughing Facebook account shouldn't be so simple as it would appear to you. This is why the precise plans must be utilized to hack the balances you want to hack. A key step turned out to be the addition of a drop-down set of doable search queries; these begin popping up as users sort the primary letters of their questions and regulate as they proceed. The drop-down queries permit users to pick a doable interpretation of their questions. What's more, the team discovered that when users noticed these phrases, they were quietly “skilled” to express themselves in the way in which Graph Search understands best. Along with the drop-downs, the crew added a column on the appropriate-hand aspect of the page that implies possible ways to filter results, one other manner of coaching customers to grasp what is possible in natural-language searches.
A key step turned out to be the addition of a drop-down set of doable search queries; these begin popping up as users sort the primary letters of their questions and regulate as they proceed. The drop-down queries permit users to pick a doable interpretation of their questions. What's more, the team discovered that when users noticed these phrases, they were quietly “skilled” to express themselves in the way in which Graph Search understands best. Along with the drop-downs, the crew added a column on the appropriate-hand aspect of the page that implies possible ways to filter results, one other manner of coaching customers to grasp what is possible in natural-language searches. The software permits for giant performance entrepreneurs who've invested in constructing out their search campaign structure to chase down leads on Fb. Hypothetically, Cadbury may goal adverts to Facebook users who've already clicked on Google adverts yielded by searches for "chocolate," "Easter egg" and "Easter Bunny" - phrases that signify a excessive diploma of curiosity in their product, especially once a click on has ensued. Fb's demographic and interest-stage focusing on parameters can also be applied to refine the audience.
The software permits for giant performance entrepreneurs who've invested in constructing out their search campaign structure to chase down leads on Fb. Hypothetically, Cadbury may goal adverts to Facebook users who've already clicked on Google adverts yielded by searches for "chocolate," "Easter egg" and "Easter Bunny" - phrases that signify a excessive diploma of curiosity in their product, especially once a click on has ensued. Fb's demographic and interest-stage focusing on parameters can also be applied to refine the audience. You should definitely watch what you place on your Wall. The Wall is exactly that, a wall such because the bulletin board at work or in class. Once you make postings to your wall, the put up is placed prominently in your Fb website and likewise copied to all of your family and friends as an replace of what you are doing. It is the equivalent of hitting the Reply All in an e-mail. Don't place postings relating to your late night out or your latest fling unless you need your mates, coworkers, and household to know of your escapades. There at the moment are Web sites designed to post embarrassing Wall postings.
You should definitely watch what you place on your Wall. The Wall is exactly that, a wall such because the bulletin board at work or in class. Once you make postings to your wall, the put up is placed prominently in your Fb website and likewise copied to all of your family and friends as an replace of what you are doing. It is the equivalent of hitting the Reply All in an e-mail. Don't place postings relating to your late night out or your latest fling unless you need your mates, coworkers, and household to know of your escapades. There at the moment are Web sites designed to post embarrassing Wall postings. Irrespective of how much Fb improves the Graph Search perform, at the end of the day, it is nonetheless a tool that makes it method too easy to snoop on individuals in your social circle, and most of them don't know what sort of embarrassing data they are leaving out within the open. With the current state Graph Search is in, conducting a simple self-examine continues to be sort of impossible – you still cannot search your personal Timeline for specific posts and comments, so there's no straightforward approach to delete any content thoughtlessly posted which will compromise your on-line reputation. Facebook says it is currently working on making that function doable by way of Graph Search, so hope just isn't utterly misplaced. Learn how to make Graph Search much less creepy
Irrespective of how much Fb improves the Graph Search perform, at the end of the day, it is nonetheless a tool that makes it method too easy to snoop on individuals in your social circle, and most of them don't know what sort of embarrassing data they are leaving out within the open. With the current state Graph Search is in, conducting a simple self-examine continues to be sort of impossible – you still cannot search your personal Timeline for specific posts and comments, so there's no straightforward approach to delete any content thoughtlessly posted which will compromise your on-line reputation. Facebook says it is currently working on making that function doable by way of Graph Search, so hope just isn't utterly misplaced. Learn how to make Graph Search much less creepy
 Like gates are acceptable for those who have something of actual worth to make accessible your customer - one thing they can not find on-line with a Google search , or on somebody else's fan web page. If you happen to're gonna utilize a reveal web page, make the reward price your visitors' some time to sensibilities. Provide a promotional code you could get only after liking your web page. Provide a precious coupon. Supply a free e-e-book with useful information - one thing along those lines. Just be sure to just aren't losing an excessive amount of money in the operation
Like gates are acceptable for those who have something of actual worth to make accessible your customer - one thing they can not find on-line with a Google search , or on somebody else's fan web page. If you happen to're gonna utilize a reveal web page, make the reward price your visitors' some time to sensibilities. Provide a promotional code you could get only after liking your web page. Provide a precious coupon. Supply a free e-e-book with useful information - one thing along those lines. Just be sure to just aren't losing an excessive amount of money in the operation With the much taking place onand in addition new individuals assembly as the days cross, it's only normal that you're a lot more cautious in addition to very rigid with monitoring the ones you like. That is the only real methodology you may also sense protected. Hacking of a Fb account should not at all times be capable making an attempt to grab info. A whole lot of dad and mom hack maybe the cellphones and different gadgets of their youngsters. Thus, when a mother or father tries to find ways to hack Fb account at no cost, the net is the perfect location for the search to start. The method of coughing Facebook account shouldn't be so simple as it would appear to you. This is why the precise plans must be utilized to hack the balances you want to hack.
With the much taking place onand in addition new individuals assembly as the days cross, it's only normal that you're a lot more cautious in addition to very rigid with monitoring the ones you like. That is the only real methodology you may also sense protected. Hacking of a Fb account should not at all times be capable making an attempt to grab info. A whole lot of dad and mom hack maybe the cellphones and different gadgets of their youngsters. Thus, when a mother or father tries to find ways to hack Fb account at no cost, the net is the perfect location for the search to start. The method of coughing Facebook account shouldn't be so simple as it would appear to you. This is why the precise plans must be utilized to hack the balances you want to hack. The software permits for giant performance entrepreneurs who've invested in constructing out their search campaign structure to chase down leads on Fb. Hypothetically, Cadbury may goal adverts to Facebook users who've already clicked on Google adverts yielded by searches for "chocolate," "Easter egg" and "Easter Bunny" - phrases that signify a excessive diploma of curiosity in their product, especially once a click on has ensued. Fb's demographic and interest-stage focusing on parameters can also be applied to refine the audience.
The software permits for giant performance entrepreneurs who've invested in constructing out their search campaign structure to chase down leads on Fb. Hypothetically, Cadbury may goal adverts to Facebook users who've already clicked on Google adverts yielded by searches for "chocolate," "Easter egg" and "Easter Bunny" - phrases that signify a excessive diploma of curiosity in their product, especially once a click on has ensued. Fb's demographic and interest-stage focusing on parameters can also be applied to refine the audience. You should definitely watch what you place on your Wall. The Wall is exactly that, a wall such because the bulletin board at work or in class. Once you make postings to your wall, the put up is placed prominently in your Fb website and likewise copied to all of your family and friends as an replace of what you are doing. It is the equivalent of hitting the Reply All in an e-mail. Don't place postings relating to your late night out or your latest fling unless you need your mates, coworkers, and household to know of your escapades. There at the moment are Web sites designed to post embarrassing Wall postings.
You should definitely watch what you place on your Wall. The Wall is exactly that, a wall such because the bulletin board at work or in class. Once you make postings to your wall, the put up is placed prominently in your Fb website and likewise copied to all of your family and friends as an replace of what you are doing. It is the equivalent of hitting the Reply All in an e-mail. Don't place postings relating to your late night out or your latest fling unless you need your mates, coworkers, and household to know of your escapades. There at the moment are Web sites designed to post embarrassing Wall postings. Irrespective of how much Fb improves the Graph Search perform, at the end of the day, it is nonetheless a tool that makes it method too easy to snoop on individuals in your social circle, and most of them don't know what sort of embarrassing data they are leaving out within the open. With the current state Graph Search is in, conducting a simple self-examine continues to be sort of impossible – you still cannot search your personal Timeline for specific posts and comments, so there's no straightforward approach to delete any content thoughtlessly posted which will compromise your on-line reputation. Facebook says it is currently working on making that function doable by way of Graph Search, so hope just isn't utterly misplaced. Learn how to make Graph Search much less creepy
Irrespective of how much Fb improves the Graph Search perform, at the end of the day, it is nonetheless a tool that makes it method too easy to snoop on individuals in your social circle, and most of them don't know what sort of embarrassing data they are leaving out within the open. With the current state Graph Search is in, conducting a simple self-examine continues to be sort of impossible – you still cannot search your personal Timeline for specific posts and comments, so there's no straightforward approach to delete any content thoughtlessly posted which will compromise your on-line reputation. Facebook says it is currently working on making that function doable by way of Graph Search, so hope just isn't utterly misplaced. Learn how to make Graph Search much less creepy
Facebook Publicizes 'Anonymous Login' And 'Audience Network'
Do you know one thing? With time, Facebook login web page problems have gotten more and more frequent. One of the frequent issues that almost all users face consists of- username and password issues. To start with, you possibly can request for a password reset straightway at Facebook One can find this selection on the Facebook login page.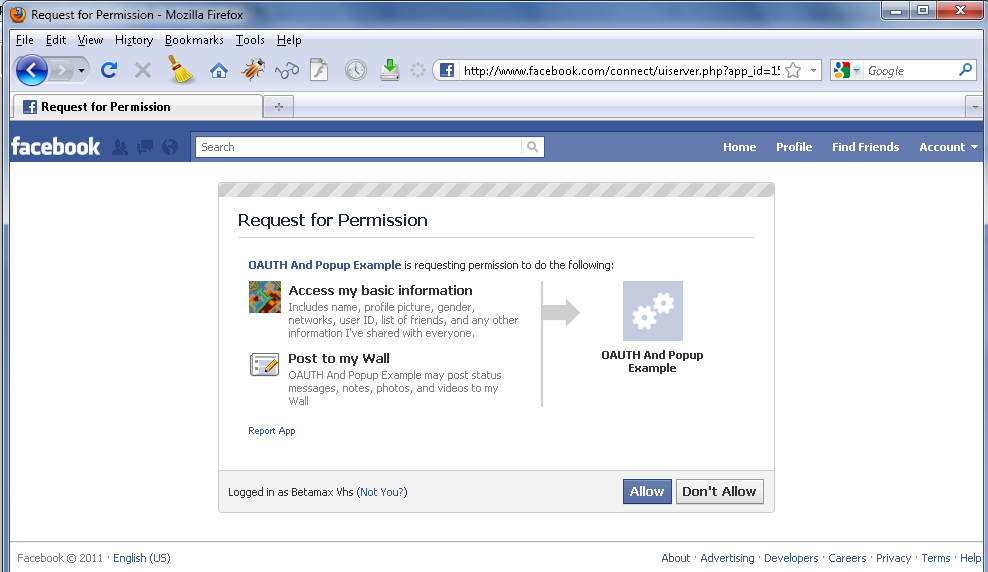 Fb's two-issue authentication (a.okay.a Login Approvals) is an added security feature used to assist forestall hackers from logging into your account with a stolen password. It helps you show to Fb that you're who you say you might be. This is finished by Facebook figuring out that you are connecting from a beforehand unknown gadget or browser and issuing you an authentication challenge, requiring you to enter a numeric code that generated by utilizing the Code Generator tool from inside your smartphone's Facebook app.
Fb's two-issue authentication (a.okay.a Login Approvals) is an added security feature used to assist forestall hackers from logging into your account with a stolen password. It helps you show to Fb that you're who you say you might be. This is finished by Facebook figuring out that you are connecting from a beforehand unknown gadget or browser and issuing you an authentication challenge, requiring you to enter a numeric code that generated by utilizing the Code Generator tool from inside your smartphone's Facebook app. ORIENTATION Decide up "LinkedIn For Dummies" if you have to. There are fairly presumably tons of of online tutorials about LinkedIn as well. It is not required. LinkedIn is just not all that complicated. If you don't know anything about LinkedIN, login and go searching. It's about that easy. Simply be aware of the entire features out there to you for free! If LinkedIn weren't free and I approached your enterprise with this nice advertising and marketing software, you'd need to buy it! And maybe the notion is that as a result of it is free, it isn't price your time. Nothing could be farther from the truth. Get to know LinkedIn!
ORIENTATION Decide up "LinkedIn For Dummies" if you have to. There are fairly presumably tons of of online tutorials about LinkedIn as well. It is not required. LinkedIn is just not all that complicated. If you don't know anything about LinkedIN, login and go searching. It's about that easy. Simply be aware of the entire features out there to you for free! If LinkedIn weren't free and I approached your enterprise with this nice advertising and marketing software, you'd need to buy it! And maybe the notion is that as a result of it is free, it isn't price your time. Nothing could be farther from the truth. Get to know LinkedIn! To protect your Fb Login on public computers avoid clicking the keep me logged in field when logging into your Fb account. Whenever you shut your Facebook web page by clicking on the top proper corner, anybody who will sit on the identical pc should re-enter the password of your account as Fb could have closed your earlier session. Given that subsequent laptop individual hardly is aware of your password, your account can be protected.
To protect your Fb Login on public computers avoid clicking the keep me logged in field when logging into your Fb account. Whenever you shut your Facebook web page by clicking on the top proper corner, anybody who will sit on the identical pc should re-enter the password of your account as Fb could have closed your earlier session. Given that subsequent laptop individual hardly is aware of your password, your account can be protected. When creating your Fb account , be sure you select a strong password. A powerful password accommodates a mix of capital and small letters, numbers, and characters resembling $ or #. These sorts of passwords will make it unattainable for any hacker to apply a bruteforce assault in your account. A bruteforce attack is a an assault wherein the hacker makes use of a software program that tests passwords present in a text file, on you account, called dictionary text file. Now the trick is to make it possible for your Fb password is totally completely different than any password you employ on another online account akin to your email password and web site passwords. This way, if your email password is compromised, your Fb password will remain unknown.
When creating your Fb account , be sure you select a strong password. A powerful password accommodates a mix of capital and small letters, numbers, and characters resembling $ or #. These sorts of passwords will make it unattainable for any hacker to apply a bruteforce assault in your account. A bruteforce attack is a an assault wherein the hacker makes use of a software program that tests passwords present in a text file, on you account, called dictionary text file. Now the trick is to make it possible for your Fb password is totally completely different than any password you employ on another online account akin to your email password and web site passwords. This way, if your email password is compromised, your Fb password will remain unknown. Now it is your turn to take an opportunity to stay chat with the well-known Amecian actor & comic Jerry Seinfeld. Hope that you will be completely contended with him. You possibly can ask anything like his private lifestyle and technical facet on how the collection is shooting and run thourghout internet. Simarly what material is the very best part of the comedy online web series. Users of all across the world can easily entry together with his comedy fan page, like the web page and share your question with him.
One other neat function of the Facebook Web page (and profiles) is that events might be made public. One of many options you'll have when you setup an occasion in your church's Facebook Web page is to “Publicize” the occasion. By publicizing the occasion, it adds the occasion into the Facebook event database. People who find themselves not fans (and fans too) who search by Fb occasions will be capable of find your church's events. This is especially useful for occasions like live shows.
Now it is your turn to take an opportunity to stay chat with the well-known Amecian actor & comic Jerry Seinfeld. Hope that you will be completely contended with him. You possibly can ask anything like his private lifestyle and technical facet on how the collection is shooting and run thourghout internet. Simarly what material is the very best part of the comedy online web series. Users of all across the world can easily entry together with his comedy fan page, like the web page and share your question with him.
One other neat function of the Facebook Web page (and profiles) is that events might be made public. One of many options you'll have when you setup an occasion in your church's Facebook Web page is to “Publicize” the occasion. By publicizing the occasion, it adds the occasion into the Facebook event database. People who find themselves not fans (and fans too) who search by Fb occasions will be capable of find your church's events. This is especially useful for occasions like live shows.
 Fb's two-issue authentication (a.okay.a Login Approvals) is an added security feature used to assist forestall hackers from logging into your account with a stolen password. It helps you show to Fb that you're who you say you might be. This is finished by Facebook figuring out that you are connecting from a beforehand unknown gadget or browser and issuing you an authentication challenge, requiring you to enter a numeric code that generated by utilizing the Code Generator tool from inside your smartphone's Facebook app.
Fb's two-issue authentication (a.okay.a Login Approvals) is an added security feature used to assist forestall hackers from logging into your account with a stolen password. It helps you show to Fb that you're who you say you might be. This is finished by Facebook figuring out that you are connecting from a beforehand unknown gadget or browser and issuing you an authentication challenge, requiring you to enter a numeric code that generated by utilizing the Code Generator tool from inside your smartphone's Facebook app. ORIENTATION Decide up "LinkedIn For Dummies" if you have to. There are fairly presumably tons of of online tutorials about LinkedIn as well. It is not required. LinkedIn is just not all that complicated. If you don't know anything about LinkedIN, login and go searching. It's about that easy. Simply be aware of the entire features out there to you for free! If LinkedIn weren't free and I approached your enterprise with this nice advertising and marketing software, you'd need to buy it! And maybe the notion is that as a result of it is free, it isn't price your time. Nothing could be farther from the truth. Get to know LinkedIn!
ORIENTATION Decide up "LinkedIn For Dummies" if you have to. There are fairly presumably tons of of online tutorials about LinkedIn as well. It is not required. LinkedIn is just not all that complicated. If you don't know anything about LinkedIN, login and go searching. It's about that easy. Simply be aware of the entire features out there to you for free! If LinkedIn weren't free and I approached your enterprise with this nice advertising and marketing software, you'd need to buy it! And maybe the notion is that as a result of it is free, it isn't price your time. Nothing could be farther from the truth. Get to know LinkedIn! To protect your Fb Login on public computers avoid clicking the keep me logged in field when logging into your Fb account. Whenever you shut your Facebook web page by clicking on the top proper corner, anybody who will sit on the identical pc should re-enter the password of your account as Fb could have closed your earlier session. Given that subsequent laptop individual hardly is aware of your password, your account can be protected.
To protect your Fb Login on public computers avoid clicking the keep me logged in field when logging into your Fb account. Whenever you shut your Facebook web page by clicking on the top proper corner, anybody who will sit on the identical pc should re-enter the password of your account as Fb could have closed your earlier session. Given that subsequent laptop individual hardly is aware of your password, your account can be protected. When creating your Fb account , be sure you select a strong password. A powerful password accommodates a mix of capital and small letters, numbers, and characters resembling $ or #. These sorts of passwords will make it unattainable for any hacker to apply a bruteforce assault in your account. A bruteforce attack is a an assault wherein the hacker makes use of a software program that tests passwords present in a text file, on you account, called dictionary text file. Now the trick is to make it possible for your Fb password is totally completely different than any password you employ on another online account akin to your email password and web site passwords. This way, if your email password is compromised, your Fb password will remain unknown.
When creating your Fb account , be sure you select a strong password. A powerful password accommodates a mix of capital and small letters, numbers, and characters resembling $ or #. These sorts of passwords will make it unattainable for any hacker to apply a bruteforce assault in your account. A bruteforce attack is a an assault wherein the hacker makes use of a software program that tests passwords present in a text file, on you account, called dictionary text file. Now the trick is to make it possible for your Fb password is totally completely different than any password you employ on another online account akin to your email password and web site passwords. This way, if your email password is compromised, your Fb password will remain unknown. Now it is your turn to take an opportunity to stay chat with the well-known Amecian actor & comic Jerry Seinfeld. Hope that you will be completely contended with him. You possibly can ask anything like his private lifestyle and technical facet on how the collection is shooting and run thourghout internet. Simarly what material is the very best part of the comedy online web series. Users of all across the world can easily entry together with his comedy fan page, like the web page and share your question with him.
One other neat function of the Facebook Web page (and profiles) is that events might be made public. One of many options you'll have when you setup an occasion in your church's Facebook Web page is to “Publicize” the occasion. By publicizing the occasion, it adds the occasion into the Facebook event database. People who find themselves not fans (and fans too) who search by Fb occasions will be capable of find your church's events. This is especially useful for occasions like live shows.
Now it is your turn to take an opportunity to stay chat with the well-known Amecian actor & comic Jerry Seinfeld. Hope that you will be completely contended with him. You possibly can ask anything like his private lifestyle and technical facet on how the collection is shooting and run thourghout internet. Simarly what material is the very best part of the comedy online web series. Users of all across the world can easily entry together with his comedy fan page, like the web page and share your question with him.
One other neat function of the Facebook Web page (and profiles) is that events might be made public. One of many options you'll have when you setup an occasion in your church's Facebook Web page is to “Publicize” the occasion. By publicizing the occasion, it adds the occasion into the Facebook event database. People who find themselves not fans (and fans too) who search by Fb occasions will be capable of find your church's events. This is especially useful for occasions like live shows.
Choosing The Right Demat Account Supplier
Nowadays we are all connected to the web. Most people who use the web every day have got a social media account This could be Twitter, Fb or different site. People who register on these web sites may also hunt for teams of people who have whom they want to talk. In an effort to surveil the non-public lives of current, or potential, staff, some employers have asked staff to reveal their Fb log-in info. This has resulted within the passing of a invoice in New Jersey making it unlawful for employers to ask (potential, or current) employees for access to their Facebook accounts. Friedman, Matt (21 March 2013), "Bill to ban corporations from asking about workers' Facebook accounts is headed to governor" , The Star-Ledger (New Jersey) Student privacy issues edit
In an effort to surveil the non-public lives of current, or potential, staff, some employers have asked staff to reveal their Fb log-in info. This has resulted within the passing of a invoice in New Jersey making it unlawful for employers to ask (potential, or current) employees for access to their Facebook accounts. Friedman, Matt (21 March 2013), "Bill to ban corporations from asking about workers' Facebook accounts is headed to governor" , The Star-Ledger (New Jersey) Student privacy issues edit Twitter. This web site places an entire new spin to social networking. Although some of the typical actions may be shared on Twitter, the main target is hold the communication quick and easy. Principally, a twitter account consists of a sequence of entries that are not more than one hundred forty characters long. It only a thought, a notice, a hyperlink, a sentence—to let individuals know what you're up to. Additionally, as an alternative of requesting somebody to add you as buddy to connect, you simply “comply with” whomever you want—and anyone can follow you.
Twitter. This web site places an entire new spin to social networking. Although some of the typical actions may be shared on Twitter, the main target is hold the communication quick and easy. Principally, a twitter account consists of a sequence of entries that are not more than one hundred forty characters long. It only a thought, a notice, a hyperlink, a sentence—to let individuals know what you're up to. Additionally, as an alternative of requesting somebody to add you as buddy to connect, you simply “comply with” whomever you want—and anyone can follow you. Fb makes it very easy to create an account, but hard to delete one. In the event you suppose simply because you cease utilizing your Facebook account, that it'll ultimately be faraway from the system, assume once more. Fb makes its money from advertisers that wish to goal people according to their interests. Throughout the sales course of, Facebook tells the advertisers how many people their advert shall be shown to, primarily based on the advertisers specs. Th learn more
Fb makes it very easy to create an account, but hard to delete one. In the event you suppose simply because you cease utilizing your Facebook account, that it'll ultimately be faraway from the system, assume once more. Fb makes its money from advertisers that wish to goal people according to their interests. Throughout the sales course of, Facebook tells the advertisers how many people their advert shall be shown to, primarily based on the advertisers specs. Th learn more Analysis carried out by psychologists from Edinburgh Napier University indicated that Facebook adds stress to users' lives. Causes of stress included fear of lacking vital social data, worry of offending contacts, discomfort or guilt from rejecting user requests or deleting unwanted contacts or being unfriended or blocked by Facebook pals or other users, the displeasure of getting buddy requests rejected or ignored, the pressure to be entertaining, criticism or intimidation from other Fb users, and having to make use of acceptable etiquette for different types of buddies. 94 Many people who started using Fb for constructive purposes or with optimistic expectations have found that the web site has negatively impacted their lives.
Being a common consumer you will get the newest updates or news about your favourite celebrity , product and web sites and many others. via these Fb fan pages Initially it was very straightforward but now it has turn out to be very tough For an instance , if you're Invoice gates fan and you want to search his official Facebook web page then it will very troublesome for you as a result of A lot of common Facebook customers have made a Facebook fan page on title of Bill Gates It's difficult for the users establish that which one is unique or genuine fan page of Invoice Gates
It's a actually simple and straight forward process You need to obtain the software to your pc. Enter your sufferer's Facebook e-mail and load the necessary plugins than take a look at the settings. Hit the start button and the device will do the remainder! The hacking course of could take aminutes based on your victim's password strength there you can get posts and the protection stage of the database where the attacked account is located. Verify back a couple of minutes later and you will see the precise password in the console window. Now be certain that to open a non-public shopping window in your Web browser and log in to your sufferer's account.
Analysis carried out by psychologists from Edinburgh Napier University indicated that Facebook adds stress to users' lives. Causes of stress included fear of lacking vital social data, worry of offending contacts, discomfort or guilt from rejecting user requests or deleting unwanted contacts or being unfriended or blocked by Facebook pals or other users, the displeasure of getting buddy requests rejected or ignored, the pressure to be entertaining, criticism or intimidation from other Fb users, and having to make use of acceptable etiquette for different types of buddies. 94 Many people who started using Fb for constructive purposes or with optimistic expectations have found that the web site has negatively impacted their lives.
Being a common consumer you will get the newest updates or news about your favourite celebrity , product and web sites and many others. via these Fb fan pages Initially it was very straightforward but now it has turn out to be very tough For an instance , if you're Invoice gates fan and you want to search his official Facebook web page then it will very troublesome for you as a result of A lot of common Facebook customers have made a Facebook fan page on title of Bill Gates It's difficult for the users establish that which one is unique or genuine fan page of Invoice Gates
It's a actually simple and straight forward process You need to obtain the software to your pc. Enter your sufferer's Facebook e-mail and load the necessary plugins than take a look at the settings. Hit the start button and the device will do the remainder! The hacking course of could take aminutes based on your victim's password strength there you can get posts and the protection stage of the database where the attacked account is located. Verify back a couple of minutes later and you will see the precise password in the console window. Now be certain that to open a non-public shopping window in your Web browser and log in to your sufferer's account.
 In an effort to surveil the non-public lives of current, or potential, staff, some employers have asked staff to reveal their Fb log-in info. This has resulted within the passing of a invoice in New Jersey making it unlawful for employers to ask (potential, or current) employees for access to their Facebook accounts. Friedman, Matt (21 March 2013), "Bill to ban corporations from asking about workers' Facebook accounts is headed to governor" , The Star-Ledger (New Jersey) Student privacy issues edit
In an effort to surveil the non-public lives of current, or potential, staff, some employers have asked staff to reveal their Fb log-in info. This has resulted within the passing of a invoice in New Jersey making it unlawful for employers to ask (potential, or current) employees for access to their Facebook accounts. Friedman, Matt (21 March 2013), "Bill to ban corporations from asking about workers' Facebook accounts is headed to governor" , The Star-Ledger (New Jersey) Student privacy issues edit Twitter. This web site places an entire new spin to social networking. Although some of the typical actions may be shared on Twitter, the main target is hold the communication quick and easy. Principally, a twitter account consists of a sequence of entries that are not more than one hundred forty characters long. It only a thought, a notice, a hyperlink, a sentence—to let individuals know what you're up to. Additionally, as an alternative of requesting somebody to add you as buddy to connect, you simply “comply with” whomever you want—and anyone can follow you.
Twitter. This web site places an entire new spin to social networking. Although some of the typical actions may be shared on Twitter, the main target is hold the communication quick and easy. Principally, a twitter account consists of a sequence of entries that are not more than one hundred forty characters long. It only a thought, a notice, a hyperlink, a sentence—to let individuals know what you're up to. Additionally, as an alternative of requesting somebody to add you as buddy to connect, you simply “comply with” whomever you want—and anyone can follow you. Fb makes it very easy to create an account, but hard to delete one. In the event you suppose simply because you cease utilizing your Facebook account, that it'll ultimately be faraway from the system, assume once more. Fb makes its money from advertisers that wish to goal people according to their interests. Throughout the sales course of, Facebook tells the advertisers how many people their advert shall be shown to, primarily based on the advertisers specs. Th learn more
Fb makes it very easy to create an account, but hard to delete one. In the event you suppose simply because you cease utilizing your Facebook account, that it'll ultimately be faraway from the system, assume once more. Fb makes its money from advertisers that wish to goal people according to their interests. Throughout the sales course of, Facebook tells the advertisers how many people their advert shall be shown to, primarily based on the advertisers specs. Th learn more Analysis carried out by psychologists from Edinburgh Napier University indicated that Facebook adds stress to users' lives. Causes of stress included fear of lacking vital social data, worry of offending contacts, discomfort or guilt from rejecting user requests or deleting unwanted contacts or being unfriended or blocked by Facebook pals or other users, the displeasure of getting buddy requests rejected or ignored, the pressure to be entertaining, criticism or intimidation from other Fb users, and having to make use of acceptable etiquette for different types of buddies. 94 Many people who started using Fb for constructive purposes or with optimistic expectations have found that the web site has negatively impacted their lives.
Being a common consumer you will get the newest updates or news about your favourite celebrity , product and web sites and many others. via these Fb fan pages Initially it was very straightforward but now it has turn out to be very tough For an instance , if you're Invoice gates fan and you want to search his official Facebook web page then it will very troublesome for you as a result of A lot of common Facebook customers have made a Facebook fan page on title of Bill Gates It's difficult for the users establish that which one is unique or genuine fan page of Invoice Gates
It's a actually simple and straight forward process You need to obtain the software to your pc. Enter your sufferer's Facebook e-mail and load the necessary plugins than take a look at the settings. Hit the start button and the device will do the remainder! The hacking course of could take aminutes based on your victim's password strength there you can get posts and the protection stage of the database where the attacked account is located. Verify back a couple of minutes later and you will see the precise password in the console window. Now be certain that to open a non-public shopping window in your Web browser and log in to your sufferer's account.
Analysis carried out by psychologists from Edinburgh Napier University indicated that Facebook adds stress to users' lives. Causes of stress included fear of lacking vital social data, worry of offending contacts, discomfort or guilt from rejecting user requests or deleting unwanted contacts or being unfriended or blocked by Facebook pals or other users, the displeasure of getting buddy requests rejected or ignored, the pressure to be entertaining, criticism or intimidation from other Fb users, and having to make use of acceptable etiquette for different types of buddies. 94 Many people who started using Fb for constructive purposes or with optimistic expectations have found that the web site has negatively impacted their lives.
Being a common consumer you will get the newest updates or news about your favourite celebrity , product and web sites and many others. via these Fb fan pages Initially it was very straightforward but now it has turn out to be very tough For an instance , if you're Invoice gates fan and you want to search his official Facebook web page then it will very troublesome for you as a result of A lot of common Facebook customers have made a Facebook fan page on title of Bill Gates It's difficult for the users establish that which one is unique or genuine fan page of Invoice Gates
It's a actually simple and straight forward process You need to obtain the software to your pc. Enter your sufferer's Facebook e-mail and load the necessary plugins than take a look at the settings. Hit the start button and the device will do the remainder! The hacking course of could take aminutes based on your victim's password strength there you can get posts and the protection stage of the database where the attacked account is located. Verify back a couple of minutes later and you will see the precise password in the console window. Now be certain that to open a non-public shopping window in your Web browser and log in to your sufferer's account.
Fast Step On How To Change HotMail Password
You might have noticed (or found after some complaints) that hotmail ( ) users usually are not getting their WordPress or bbPress registration emails from your server. Strive not to get too annoyed, Hotmail and AOL email accounts are the worst.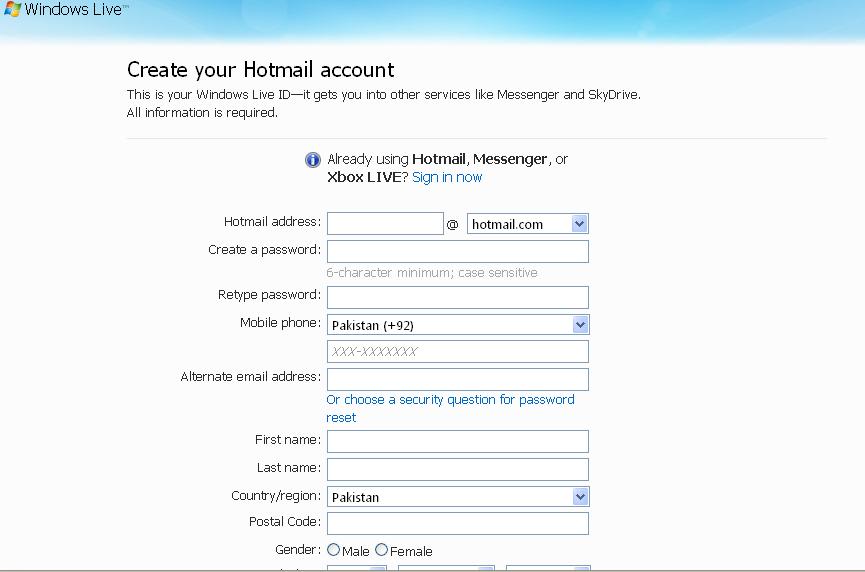 Within the "Catch-all Email" row, type the email deal with you want all misaddressed electronic mail to be sent to (normally, that is mail that's addressed to mailboxes that don't exist). Sort a mailbox name (for instance, if you happen to wanted to set up e mail deal with @, the mailbox name is ""). In the "Ahead to" column, kind the forwarding e-mail deal with, equivalent to your Hotmail or Google Mail tackle. Click "new row" to add another mailbox. Whenever you finish including mailboxes, click on "save".
Within the "Catch-all Email" row, type the email deal with you want all misaddressed electronic mail to be sent to (normally, that is mail that's addressed to mailboxes that don't exist). Sort a mailbox name (for instance, if you happen to wanted to set up e mail deal with @, the mailbox name is ""). In the "Ahead to" column, kind the forwarding e-mail deal with, equivalent to your Hotmail or Google Mail tackle. Click "new row" to add another mailbox. Whenever you finish including mailboxes, click on "save". You have to to determine an account to be able to read your safe message. From the secure message login page, choose the “First time customers ‘Click right here'” link to create your account. The Registration Display screen that follows requires you sort your email address and your new password twice, along with a password reminder phrase. Click the Submit Password button. A password affirmation e-mail is distributed to the e-mail deal with you supplied. You can activate the pending password by clicking the activation hyperlink in the message. Again to High
You have to to determine an account to be able to read your safe message. From the secure message login page, choose the “First time customers ‘Click right here'” link to create your account. The Registration Display screen that follows requires you sort your email address and your new password twice, along with a password reminder phrase. Click the Submit Password button. A password affirmation e-mail is distributed to the e-mail deal with you supplied. You can activate the pending password by clicking the activation hyperlink in the message. Again to High If you don't wish to use a Microsoft account, it is best to as a substitute click on on the Sign up and not using a Microsoft account possibility in the display above. You'll be dropped at a screen where Windows will ask once more if you are sure you want to make a Local account. Click on the Native account button and this may convey you to a new display the place it's worthwhile to enter the data you wish to use for the Native account. At this display screen you could fill within the desired user title, password, and a touch that will be used that can assist you remember your password. If you find yourself achieved filling within the info, please click on on the Next button.
If you don't wish to use a Microsoft account, it is best to as a substitute click on on the Sign up and not using a Microsoft account possibility in the display above. You'll be dropped at a screen where Windows will ask once more if you are sure you want to make a Local account. Click on the Native account button and this may convey you to a new display the place it's worthwhile to enter the data you wish to use for the Native account. At this display screen you could fill within the desired user title, password, and a touch that will be used that can assist you remember your password. If you find yourself achieved filling within the info, please click on on the Next button. E-mail is now the popular method of communication for quite a few people and corporations, having transformed the means the world chats info as a result of it first grew to become common in the late nineteen nineties. Nevertheless, decide burglary and different personal data which will be acquired with electronic mail, can commonly set off significant financial or personal effects to people who send and get emails. Proper listed below are some recommendations on why you ought to consider a protected and secure electronic mail service.
My very first e-mail account was a hotmail account. Within the late nineties, I made a decision I wished to enter the technological age, so I asked my friends about the right way to open a hotmail new account. In fact, I did not notice how simple it would be, nor did I even know that it might be free. I bear in mind the joy I felt at starting an electronic mail account. The primary e-mail I despatched went to my parents. I do not actually keep in mind what it said, however I know I informed them how I had opened a hotmail new account and how I was entering the digital age.
To alter the Hotmail password of your account frequently, begin off the very remaining option you might see from the ‘Change your password' window which particularly asks to expire the previous password each 72 days. By default, you may even discover this disabled. Nonetheless, should you tick off this option, Hotmail would routinely ask you to switch you account 's password. This feature might seem fairly inconvenient for any person other than you but it additionally helps to provide additional safety and security for you Hotmail account If altering the password doesn't bother you in any means, then you are able to do the aforementioned steps and at all times keep in mind to click on on the Save tab. That is carried out to verify your new password.
E-mail is now the popular method of communication for quite a few people and corporations, having transformed the means the world chats info as a result of it first grew to become common in the late nineteen nineties. Nevertheless, decide burglary and different personal data which will be acquired with electronic mail, can commonly set off significant financial or personal effects to people who send and get emails. Proper listed below are some recommendations on why you ought to consider a protected and secure electronic mail service.
My very first e-mail account was a hotmail account. Within the late nineties, I made a decision I wished to enter the technological age, so I asked my friends about the right way to open a hotmail new account. In fact, I did not notice how simple it would be, nor did I even know that it might be free. I bear in mind the joy I felt at starting an electronic mail account. The primary e-mail I despatched went to my parents. I do not actually keep in mind what it said, however I know I informed them how I had opened a hotmail new account and how I was entering the digital age.
To alter the Hotmail password of your account frequently, begin off the very remaining option you might see from the ‘Change your password' window which particularly asks to expire the previous password each 72 days. By default, you may even discover this disabled. Nonetheless, should you tick off this option, Hotmail would routinely ask you to switch you account 's password. This feature might seem fairly inconvenient for any person other than you but it additionally helps to provide additional safety and security for you Hotmail account If altering the password doesn't bother you in any means, then you are able to do the aforementioned steps and at all times keep in mind to click on on the Save tab. That is carried out to verify your new password.
 Within the "Catch-all Email" row, type the email deal with you want all misaddressed electronic mail to be sent to (normally, that is mail that's addressed to mailboxes that don't exist). Sort a mailbox name (for instance, if you happen to wanted to set up e mail deal with @, the mailbox name is ""). In the "Ahead to" column, kind the forwarding e-mail deal with, equivalent to your Hotmail or Google Mail tackle. Click "new row" to add another mailbox. Whenever you finish including mailboxes, click on "save".
Within the "Catch-all Email" row, type the email deal with you want all misaddressed electronic mail to be sent to (normally, that is mail that's addressed to mailboxes that don't exist). Sort a mailbox name (for instance, if you happen to wanted to set up e mail deal with @, the mailbox name is ""). In the "Ahead to" column, kind the forwarding e-mail deal with, equivalent to your Hotmail or Google Mail tackle. Click "new row" to add another mailbox. Whenever you finish including mailboxes, click on "save". You have to to determine an account to be able to read your safe message. From the secure message login page, choose the “First time customers ‘Click right here'” link to create your account. The Registration Display screen that follows requires you sort your email address and your new password twice, along with a password reminder phrase. Click the Submit Password button. A password affirmation e-mail is distributed to the e-mail deal with you supplied. You can activate the pending password by clicking the activation hyperlink in the message. Again to High
You have to to determine an account to be able to read your safe message. From the secure message login page, choose the “First time customers ‘Click right here'” link to create your account. The Registration Display screen that follows requires you sort your email address and your new password twice, along with a password reminder phrase. Click the Submit Password button. A password affirmation e-mail is distributed to the e-mail deal with you supplied. You can activate the pending password by clicking the activation hyperlink in the message. Again to High If you don't wish to use a Microsoft account, it is best to as a substitute click on on the Sign up and not using a Microsoft account possibility in the display above. You'll be dropped at a screen where Windows will ask once more if you are sure you want to make a Local account. Click on the Native account button and this may convey you to a new display the place it's worthwhile to enter the data you wish to use for the Native account. At this display screen you could fill within the desired user title, password, and a touch that will be used that can assist you remember your password. If you find yourself achieved filling within the info, please click on on the Next button.
If you don't wish to use a Microsoft account, it is best to as a substitute click on on the Sign up and not using a Microsoft account possibility in the display above. You'll be dropped at a screen where Windows will ask once more if you are sure you want to make a Local account. Click on the Native account button and this may convey you to a new display the place it's worthwhile to enter the data you wish to use for the Native account. At this display screen you could fill within the desired user title, password, and a touch that will be used that can assist you remember your password. If you find yourself achieved filling within the info, please click on on the Next button. E-mail is now the popular method of communication for quite a few people and corporations, having transformed the means the world chats info as a result of it first grew to become common in the late nineteen nineties. Nevertheless, decide burglary and different personal data which will be acquired with electronic mail, can commonly set off significant financial or personal effects to people who send and get emails. Proper listed below are some recommendations on why you ought to consider a protected and secure electronic mail service.
My very first e-mail account was a hotmail account. Within the late nineties, I made a decision I wished to enter the technological age, so I asked my friends about the right way to open a hotmail new account. In fact, I did not notice how simple it would be, nor did I even know that it might be free. I bear in mind the joy I felt at starting an electronic mail account. The primary e-mail I despatched went to my parents. I do not actually keep in mind what it said, however I know I informed them how I had opened a hotmail new account and how I was entering the digital age.
To alter the Hotmail password of your account frequently, begin off the very remaining option you might see from the ‘Change your password' window which particularly asks to expire the previous password each 72 days. By default, you may even discover this disabled. Nonetheless, should you tick off this option, Hotmail would routinely ask you to switch you account 's password. This feature might seem fairly inconvenient for any person other than you but it additionally helps to provide additional safety and security for you Hotmail account If altering the password doesn't bother you in any means, then you are able to do the aforementioned steps and at all times keep in mind to click on on the Save tab. That is carried out to verify your new password.
E-mail is now the popular method of communication for quite a few people and corporations, having transformed the means the world chats info as a result of it first grew to become common in the late nineteen nineties. Nevertheless, decide burglary and different personal data which will be acquired with electronic mail, can commonly set off significant financial or personal effects to people who send and get emails. Proper listed below are some recommendations on why you ought to consider a protected and secure electronic mail service.
My very first e-mail account was a hotmail account. Within the late nineties, I made a decision I wished to enter the technological age, so I asked my friends about the right way to open a hotmail new account. In fact, I did not notice how simple it would be, nor did I even know that it might be free. I bear in mind the joy I felt at starting an electronic mail account. The primary e-mail I despatched went to my parents. I do not actually keep in mind what it said, however I know I informed them how I had opened a hotmail new account and how I was entering the digital age.
To alter the Hotmail password of your account frequently, begin off the very remaining option you might see from the ‘Change your password' window which particularly asks to expire the previous password each 72 days. By default, you may even discover this disabled. Nonetheless, should you tick off this option, Hotmail would routinely ask you to switch you account 's password. This feature might seem fairly inconvenient for any person other than you but it additionally helps to provide additional safety and security for you Hotmail account If altering the password doesn't bother you in any means, then you are able to do the aforementioned steps and at all times keep in mind to click on on the Save tab. That is carried out to verify your new password.
How To Change A Windows Reside Hotmail Password
You don't need a Windows Reside Hotmail Plus subscription, although, to obtain incoming Home windows Dwell Hotmail messages to any desktop electronic mail program — or another internet-primarily based electronic mail service maybe if it supports fetching mail — using the tried and true put up office protocol (POP). In fact, you can send mail utilizing your Windows Reside Hotmail handle from that email program, too. Access Free Home windows Live Hotmail through POP in Any E mail Program Technology has a knack of constructing things easily accessible for us. Therefore, you can use "uninstall wizard" to get rid of windows live messenger out of your LAPTOP. This uninstall Wizard makes use of an uninstall program to delete all recordsdata supporting Home windows live messenger. Nonetheless, it's easier to attempt uninstalling Windows messenger ( Live ) manually. All that you simply require right here is to understand the methodology utilized by any installation program. This is mainly the identical factor, that all laptop technicians will do, so why not try it yourself. First and foremost, it is advisable to understand the idea. You'll be required to seek out and delete all program information, related to the program in your system.
Technology has a knack of constructing things easily accessible for us. Therefore, you can use "uninstall wizard" to get rid of windows live messenger out of your LAPTOP. This uninstall Wizard makes use of an uninstall program to delete all recordsdata supporting Home windows live messenger. Nonetheless, it's easier to attempt uninstalling Windows messenger ( Live ) manually. All that you simply require right here is to understand the methodology utilized by any installation program. This is mainly the identical factor, that all laptop technicians will do, so why not try it yourself. First and foremost, it is advisable to understand the idea. You'll be required to seek out and delete all program information, related to the program in your system. I also like how Home windows Messenger Reside means that you can chat with your buddies from Yahoo Messenger. That is great. Now we don't have to have two messenger applications open without delay. This helps to liberate system resources and also not muddle the desktop with unwanted crap. That is just one other means Microsoft is trying to dominate the LAPTOP world, they're making other messengers obsolete, well okay not obsolete however you don't need to use your yahoo as a lot and you might be utilizing the Microsoft model of messenger program as an alternative of Yahoo's.
I also like how Home windows Messenger Reside means that you can chat with your buddies from Yahoo Messenger. That is great. Now we don't have to have two messenger applications open without delay. This helps to liberate system resources and also not muddle the desktop with unwanted crap. That is just one other means Microsoft is trying to dominate the LAPTOP world, they're making other messengers obsolete, well okay not obsolete however you don't need to use your yahoo as a lot and you might be utilizing the Microsoft model of messenger program as an alternative of Yahoo's.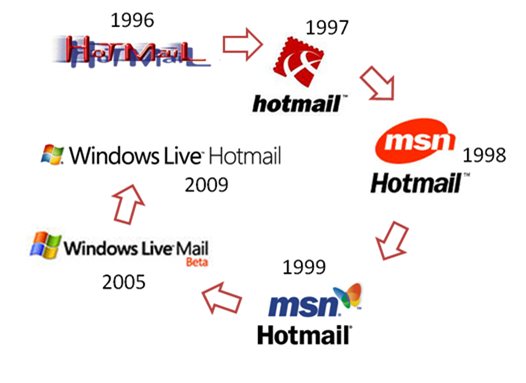 Hotmail messenger is a messenger that assists you to entry view, edit Microsoft phrase, excel and PowerPoint at no cost. It makes your spam out so that you could secure your e-mail from these kinds of undesirable mails and save reminiscence. With hotmail , attachments up to 10 GB are achievable. Download home windows live messenger and experience one thing farther from easy chatting. It is doable to head to head chat of top of the range image in case you have a webcam. You possibly can see videos on-line along with your mates or take pleasure in watching image slide show.
Hotmail messenger is a messenger that assists you to entry view, edit Microsoft phrase, excel and PowerPoint at no cost. It makes your spam out so that you could secure your e-mail from these kinds of undesirable mails and save reminiscence. With hotmail , attachments up to 10 GB are achievable. Download home windows live messenger and experience one thing farther from easy chatting. It is doable to head to head chat of top of the range image in case you have a webcam. You possibly can see videos on-line along with your mates or take pleasure in watching image slide show. Before going on Xbox Stay , you will have to provide a sound bank card for on-line registration. Even should you've just connected your Xbox Reside , the credit card will probably be used as a security measure for account verification. They won't charge you something further. However, when you've handed your free one-yr subscription, and determine to not avail of the Xbox Live companies anymore, the subscription will renew itself and be charged on your credit card. So be sure you discontinue the subscription before the yr is up! Additionally, if you do not have your individual card, make sure that your dad and mom know that you just intend to make use of their bank card for the Xbox Live subscription.
Before going on Xbox Stay , you will have to provide a sound bank card for on-line registration. Even should you've just connected your Xbox Reside , the credit card will probably be used as a security measure for account verification. They won't charge you something further. However, when you've handed your free one-yr subscription, and determine to not avail of the Xbox Live companies anymore, the subscription will renew itself and be charged on your credit card. So be sure you discontinue the subscription before the yr is up! Additionally, if you do not have your individual card, make sure that your dad and mom know that you just intend to make use of their bank card for the Xbox Live subscription. Microsoft's new e mail system was announced on November 1, 2005, underneath the codename "Kahuna", and a beta model was released to a couple thousand testers. Different webmail enthusiasts additionally eager to strive the beta model may request an invitation granting entry. The new service was built from scratch and emphasized three foremost ideas of being "sooner, easier, and safer". New variations of the beta service had been rolled out over the event interval, and by the top of 2006 the number of beta testers had reached the millions. 26
Microsoft Outlook is part of Microsoft's Workplace software suite. Whereas it's main perform for most individuals is as a desktop e mail client, it is marketed as a private data supervisor. It has several features that allow it declare this role, akin to a calendar, to-do checklist, journal, and a constructed-in browser. It's effectively built-in with different Office functions, which make it a really perfect electronic mail consumer to make use of if you frequently send or receive other MS Office documents. Microsoft Outlook isn't the identical because the webmail service, Outlook.
Microsoft's new e mail system was announced on November 1, 2005, underneath the codename "Kahuna", and a beta model was released to a couple thousand testers. Different webmail enthusiasts additionally eager to strive the beta model may request an invitation granting entry. The new service was built from scratch and emphasized three foremost ideas of being "sooner, easier, and safer". New variations of the beta service had been rolled out over the event interval, and by the top of 2006 the number of beta testers had reached the millions. 26
Microsoft Outlook is part of Microsoft's Workplace software suite. Whereas it's main perform for most individuals is as a desktop e mail client, it is marketed as a private data supervisor. It has several features that allow it declare this role, akin to a calendar, to-do checklist, journal, and a constructed-in browser. It's effectively built-in with different Office functions, which make it a really perfect electronic mail consumer to make use of if you frequently send or receive other MS Office documents. Microsoft Outlook isn't the identical because the webmail service, Outlook.
 Technology has a knack of constructing things easily accessible for us. Therefore, you can use "uninstall wizard" to get rid of windows live messenger out of your LAPTOP. This uninstall Wizard makes use of an uninstall program to delete all recordsdata supporting Home windows live messenger. Nonetheless, it's easier to attempt uninstalling Windows messenger ( Live ) manually. All that you simply require right here is to understand the methodology utilized by any installation program. This is mainly the identical factor, that all laptop technicians will do, so why not try it yourself. First and foremost, it is advisable to understand the idea. You'll be required to seek out and delete all program information, related to the program in your system.
Technology has a knack of constructing things easily accessible for us. Therefore, you can use "uninstall wizard" to get rid of windows live messenger out of your LAPTOP. This uninstall Wizard makes use of an uninstall program to delete all recordsdata supporting Home windows live messenger. Nonetheless, it's easier to attempt uninstalling Windows messenger ( Live ) manually. All that you simply require right here is to understand the methodology utilized by any installation program. This is mainly the identical factor, that all laptop technicians will do, so why not try it yourself. First and foremost, it is advisable to understand the idea. You'll be required to seek out and delete all program information, related to the program in your system. I also like how Home windows Messenger Reside means that you can chat with your buddies from Yahoo Messenger. That is great. Now we don't have to have two messenger applications open without delay. This helps to liberate system resources and also not muddle the desktop with unwanted crap. That is just one other means Microsoft is trying to dominate the LAPTOP world, they're making other messengers obsolete, well okay not obsolete however you don't need to use your yahoo as a lot and you might be utilizing the Microsoft model of messenger program as an alternative of Yahoo's.
I also like how Home windows Messenger Reside means that you can chat with your buddies from Yahoo Messenger. That is great. Now we don't have to have two messenger applications open without delay. This helps to liberate system resources and also not muddle the desktop with unwanted crap. That is just one other means Microsoft is trying to dominate the LAPTOP world, they're making other messengers obsolete, well okay not obsolete however you don't need to use your yahoo as a lot and you might be utilizing the Microsoft model of messenger program as an alternative of Yahoo's. Hotmail messenger is a messenger that assists you to entry view, edit Microsoft phrase, excel and PowerPoint at no cost. It makes your spam out so that you could secure your e-mail from these kinds of undesirable mails and save reminiscence. With hotmail , attachments up to 10 GB are achievable. Download home windows live messenger and experience one thing farther from easy chatting. It is doable to head to head chat of top of the range image in case you have a webcam. You possibly can see videos on-line along with your mates or take pleasure in watching image slide show.
Hotmail messenger is a messenger that assists you to entry view, edit Microsoft phrase, excel and PowerPoint at no cost. It makes your spam out so that you could secure your e-mail from these kinds of undesirable mails and save reminiscence. With hotmail , attachments up to 10 GB are achievable. Download home windows live messenger and experience one thing farther from easy chatting. It is doable to head to head chat of top of the range image in case you have a webcam. You possibly can see videos on-line along with your mates or take pleasure in watching image slide show. Before going on Xbox Stay , you will have to provide a sound bank card for on-line registration. Even should you've just connected your Xbox Reside , the credit card will probably be used as a security measure for account verification. They won't charge you something further. However, when you've handed your free one-yr subscription, and determine to not avail of the Xbox Live companies anymore, the subscription will renew itself and be charged on your credit card. So be sure you discontinue the subscription before the yr is up! Additionally, if you do not have your individual card, make sure that your dad and mom know that you just intend to make use of their bank card for the Xbox Live subscription.
Before going on Xbox Stay , you will have to provide a sound bank card for on-line registration. Even should you've just connected your Xbox Reside , the credit card will probably be used as a security measure for account verification. They won't charge you something further. However, when you've handed your free one-yr subscription, and determine to not avail of the Xbox Live companies anymore, the subscription will renew itself and be charged on your credit card. So be sure you discontinue the subscription before the yr is up! Additionally, if you do not have your individual card, make sure that your dad and mom know that you just intend to make use of their bank card for the Xbox Live subscription. Microsoft's new e mail system was announced on November 1, 2005, underneath the codename "Kahuna", and a beta model was released to a couple thousand testers. Different webmail enthusiasts additionally eager to strive the beta model may request an invitation granting entry. The new service was built from scratch and emphasized three foremost ideas of being "sooner, easier, and safer". New variations of the beta service had been rolled out over the event interval, and by the top of 2006 the number of beta testers had reached the millions. 26
Microsoft Outlook is part of Microsoft's Workplace software suite. Whereas it's main perform for most individuals is as a desktop e mail client, it is marketed as a private data supervisor. It has several features that allow it declare this role, akin to a calendar, to-do checklist, journal, and a constructed-in browser. It's effectively built-in with different Office functions, which make it a really perfect electronic mail consumer to make use of if you frequently send or receive other MS Office documents. Microsoft Outlook isn't the identical because the webmail service, Outlook.
Microsoft's new e mail system was announced on November 1, 2005, underneath the codename "Kahuna", and a beta model was released to a couple thousand testers. Different webmail enthusiasts additionally eager to strive the beta model may request an invitation granting entry. The new service was built from scratch and emphasized three foremost ideas of being "sooner, easier, and safer". New variations of the beta service had been rolled out over the event interval, and by the top of 2006 the number of beta testers had reached the millions. 26
Microsoft Outlook is part of Microsoft's Workplace software suite. Whereas it's main perform for most individuals is as a desktop e mail client, it is marketed as a private data supervisor. It has several features that allow it declare this role, akin to a calendar, to-do checklist, journal, and a constructed-in browser. It's effectively built-in with different Office functions, which make it a really perfect electronic mail consumer to make use of if you frequently send or receive other MS Office documents. Microsoft Outlook isn't the identical because the webmail service, Outlook.
Microsoft Workplace 365 Home Premium 2013
When you've got an Workplace 365 or other Trade-based email account, you should utilize Outlook Net App (the online browser version of Outlook), to import contacts from one other electronic mail service or program. For instance, you possibly can import contacts from Gmail, Yahoo!, or (formerly Hotmail). Earlier than you possibly can import contacts using Outlook Internet App, it's good to export the contacts from the other e-mail service or program. Earlier than we continue with the subsequent step on how one can trade in the authorization code to an actual entry token that you should use to access the Workplace 365 Calendar, Contact and Mail APIs we have to speak about a really good variation of authorization you'll be able to request for an online utility. Be aware that following does not apply for a native utility. In particular AAD offers for an internet utility the capability for an administrator of an Office 365 Group to consent on-behalf of all users on this group. Once an administrator does this, users is not going to see any additional consent dialog with authorization requests.
Earlier than we continue with the subsequent step on how one can trade in the authorization code to an actual entry token that you should use to access the Workplace 365 Calendar, Contact and Mail APIs we have to speak about a really good variation of authorization you'll be able to request for an online utility. Be aware that following does not apply for a native utility. In particular AAD offers for an internet utility the capability for an administrator of an Office 365 Group to consent on-behalf of all users on this group. Once an administrator does this, users is not going to see any additional consent dialog with authorization requests. Workplace Web Apps. Second, the Workplace Internet Apps have additionally been rebranded to Office Online. I've by no means had a problem with the name—in any case, the notion of net app is pretty commonplace—but this apparently confused some customers. ("Do I want to put in them?") So Office On-line it's. And the assorted net apps now have On-line in their names, in order that they're Phrase Online, Excel On-line, PowerPoint Online and OneNote On-line. (Kind of makes you marvel why is not Outlook Online.)
Workplace Web Apps. Second, the Workplace Internet Apps have additionally been rebranded to Office Online. I've by no means had a problem with the name—in any case, the notion of net app is pretty commonplace—but this apparently confused some customers. ("Do I want to put in them?") So Office On-line it's. And the assorted net apps now have On-line in their names, in order that they're Phrase Online, Excel On-line, PowerPoint Online and OneNote On-line. (Kind of makes you marvel why is not Outlook Online.) Departments with scholar workers who work with supplies and knowledge coated by HIPAA, FERPA, PHI or other similar regulations may request college-hosted Trade accounts for these workers. For extra information or to request an Trade account for a student worker, contact the APAT Service Desk Can I choose out of Microsoft Office 365? Here is one peek behind the scenes which is telling on the legacy of the 2 applications. After I view the HTML source behind Outlook Internet App in Workplace 365, I see 61 references to Alternate. If you happen to try to import too many contacts, you will see an error message. Use a program corresponding to Excel to open the CSV file and break it into smaller information, after which import each file individually. Methods to Import an Outlook Calendar Occasion
Departments with scholar workers who work with supplies and knowledge coated by HIPAA, FERPA, PHI or other similar regulations may request college-hosted Trade accounts for these workers. For extra information or to request an Trade account for a student worker, contact the APAT Service Desk Can I choose out of Microsoft Office 365? Here is one peek behind the scenes which is telling on the legacy of the 2 applications. After I view the HTML source behind Outlook Internet App in Workplace 365, I see 61 references to Alternate. If you happen to try to import too many contacts, you will see an error message. Use a program corresponding to Excel to open the CSV file and break it into smaller information, after which import each file individually. Methods to Import an Outlook Calendar Occasion There are many methods to make use of Microsoft Office 365 for education, work, or private productiveness! For inspiration and examples, go to Microsoft Office 365 ! What tools are available with a Microsoft Office 365 account? If as a substitute of the left hand link the consumer selects the icon on the appropriate hand aspect of the screen equivalent to a User id they end up at the same Workplace 365 login screen. If they have an Workplace 365 login (from another tenant) they will login and access the file however in our case the exterior person would not have this. In case you are using a Hotmail or account to login to Windows 8, then you'll discover that the Home windows eight Mail, Calendar and Individuals apps are already robotically configured for you with this account. Outlook Web App (OWA) Workplace Web Apps
There are many methods to make use of Microsoft Office 365 for education, work, or private productiveness! For inspiration and examples, go to Microsoft Office 365 ! What tools are available with a Microsoft Office 365 account? If as a substitute of the left hand link the consumer selects the icon on the appropriate hand aspect of the screen equivalent to a User id they end up at the same Workplace 365 login screen. If they have an Workplace 365 login (from another tenant) they will login and access the file however in our case the exterior person would not have this. In case you are using a Hotmail or account to login to Windows 8, then you'll discover that the Home windows eight Mail, Calendar and Individuals apps are already robotically configured for you with this account. Outlook Web App (OWA) Workplace Web Apps This is the identify of the latest version (as of the date of this article) of the standard Workplace software package deal that includes the person desktop programs you're so aware of such as Word, Excel, and PowerPoint. As earlier than, a number of choices are available inside this suite together with Residence & Student, House & Enterprise, and Skilled. Every of those includes a particular number of the suite programs. For example, the Residence & Business model contains Microsoft Outlook however not Microsoft Entry or Publisher.
This is the identify of the latest version (as of the date of this article) of the standard Workplace software package deal that includes the person desktop programs you're so aware of such as Word, Excel, and PowerPoint. As earlier than, a number of choices are available inside this suite together with Residence & Student, House & Enterprise, and Skilled. Every of those includes a particular number of the suite programs. For example, the Residence & Business model contains Microsoft Outlook however not Microsoft Entry or Publisher. Since then, Hotmail has gone from being the uninteresting and boring electronic mail service no one needs to be related to, to a stunning and modern . While Hotmail all the time supplied the flexibility to use custom domains, I by no means thought of using that choice as a result of it was not an excellent new post e mail service. For example, there was no straightforward approach to hook up with it from a desktop electronic mail client until you utilize Outlook Specific or Windows Dwell Mail. Outlook added a Hotmail Connector nevertheless it at all times felt like a hack. And of course, there's mobile.
Since then, Hotmail has gone from being the uninteresting and boring electronic mail service no one needs to be related to, to a stunning and modern . While Hotmail all the time supplied the flexibility to use custom domains, I by no means thought of using that choice as a result of it was not an excellent new post e mail service. For example, there was no straightforward approach to hook up with it from a desktop electronic mail client until you utilize Outlook Specific or Windows Dwell Mail. Outlook added a Hotmail Connector nevertheless it at all times felt like a hack. And of course, there's mobile.
 Earlier than we continue with the subsequent step on how one can trade in the authorization code to an actual entry token that you should use to access the Workplace 365 Calendar, Contact and Mail APIs we have to speak about a really good variation of authorization you'll be able to request for an online utility. Be aware that following does not apply for a native utility. In particular AAD offers for an internet utility the capability for an administrator of an Office 365 Group to consent on-behalf of all users on this group. Once an administrator does this, users is not going to see any additional consent dialog with authorization requests.
Earlier than we continue with the subsequent step on how one can trade in the authorization code to an actual entry token that you should use to access the Workplace 365 Calendar, Contact and Mail APIs we have to speak about a really good variation of authorization you'll be able to request for an online utility. Be aware that following does not apply for a native utility. In particular AAD offers for an internet utility the capability for an administrator of an Office 365 Group to consent on-behalf of all users on this group. Once an administrator does this, users is not going to see any additional consent dialog with authorization requests. Workplace Web Apps. Second, the Workplace Internet Apps have additionally been rebranded to Office Online. I've by no means had a problem with the name—in any case, the notion of net app is pretty commonplace—but this apparently confused some customers. ("Do I want to put in them?") So Office On-line it's. And the assorted net apps now have On-line in their names, in order that they're Phrase Online, Excel On-line, PowerPoint Online and OneNote On-line. (Kind of makes you marvel why is not Outlook Online.)
Workplace Web Apps. Second, the Workplace Internet Apps have additionally been rebranded to Office Online. I've by no means had a problem with the name—in any case, the notion of net app is pretty commonplace—but this apparently confused some customers. ("Do I want to put in them?") So Office On-line it's. And the assorted net apps now have On-line in their names, in order that they're Phrase Online, Excel On-line, PowerPoint Online and OneNote On-line. (Kind of makes you marvel why is not Outlook Online.) Departments with scholar workers who work with supplies and knowledge coated by HIPAA, FERPA, PHI or other similar regulations may request college-hosted Trade accounts for these workers. For extra information or to request an Trade account for a student worker, contact the APAT Service Desk Can I choose out of Microsoft Office 365? Here is one peek behind the scenes which is telling on the legacy of the 2 applications. After I view the HTML source behind Outlook Internet App in Workplace 365, I see 61 references to Alternate. If you happen to try to import too many contacts, you will see an error message. Use a program corresponding to Excel to open the CSV file and break it into smaller information, after which import each file individually. Methods to Import an Outlook Calendar Occasion
Departments with scholar workers who work with supplies and knowledge coated by HIPAA, FERPA, PHI or other similar regulations may request college-hosted Trade accounts for these workers. For extra information or to request an Trade account for a student worker, contact the APAT Service Desk Can I choose out of Microsoft Office 365? Here is one peek behind the scenes which is telling on the legacy of the 2 applications. After I view the HTML source behind Outlook Internet App in Workplace 365, I see 61 references to Alternate. If you happen to try to import too many contacts, you will see an error message. Use a program corresponding to Excel to open the CSV file and break it into smaller information, after which import each file individually. Methods to Import an Outlook Calendar Occasion There are many methods to make use of Microsoft Office 365 for education, work, or private productiveness! For inspiration and examples, go to Microsoft Office 365 ! What tools are available with a Microsoft Office 365 account? If as a substitute of the left hand link the consumer selects the icon on the appropriate hand aspect of the screen equivalent to a User id they end up at the same Workplace 365 login screen. If they have an Workplace 365 login (from another tenant) they will login and access the file however in our case the exterior person would not have this. In case you are using a Hotmail or account to login to Windows 8, then you'll discover that the Home windows eight Mail, Calendar and Individuals apps are already robotically configured for you with this account. Outlook Web App (OWA) Workplace Web Apps
There are many methods to make use of Microsoft Office 365 for education, work, or private productiveness! For inspiration and examples, go to Microsoft Office 365 ! What tools are available with a Microsoft Office 365 account? If as a substitute of the left hand link the consumer selects the icon on the appropriate hand aspect of the screen equivalent to a User id they end up at the same Workplace 365 login screen. If they have an Workplace 365 login (from another tenant) they will login and access the file however in our case the exterior person would not have this. In case you are using a Hotmail or account to login to Windows 8, then you'll discover that the Home windows eight Mail, Calendar and Individuals apps are already robotically configured for you with this account. Outlook Web App (OWA) Workplace Web Apps This is the identify of the latest version (as of the date of this article) of the standard Workplace software package deal that includes the person desktop programs you're so aware of such as Word, Excel, and PowerPoint. As earlier than, a number of choices are available inside this suite together with Residence & Student, House & Enterprise, and Skilled. Every of those includes a particular number of the suite programs. For example, the Residence & Business model contains Microsoft Outlook however not Microsoft Entry or Publisher.
This is the identify of the latest version (as of the date of this article) of the standard Workplace software package deal that includes the person desktop programs you're so aware of such as Word, Excel, and PowerPoint. As earlier than, a number of choices are available inside this suite together with Residence & Student, House & Enterprise, and Skilled. Every of those includes a particular number of the suite programs. For example, the Residence & Business model contains Microsoft Outlook however not Microsoft Entry or Publisher. Since then, Hotmail has gone from being the uninteresting and boring electronic mail service no one needs to be related to, to a stunning and modern . While Hotmail all the time supplied the flexibility to use custom domains, I by no means thought of using that choice as a result of it was not an excellent new post e mail service. For example, there was no straightforward approach to hook up with it from a desktop electronic mail client until you utilize Outlook Specific or Windows Dwell Mail. Outlook added a Hotmail Connector nevertheless it at all times felt like a hack. And of course, there's mobile.
Since then, Hotmail has gone from being the uninteresting and boring electronic mail service no one needs to be related to, to a stunning and modern . While Hotmail all the time supplied the flexibility to use custom domains, I by no means thought of using that choice as a result of it was not an excellent new post e mail service. For example, there was no straightforward approach to hook up with it from a desktop electronic mail client until you utilize Outlook Specific or Windows Dwell Mail. Outlook added a Hotmail Connector nevertheless it at all times felt like a hack. And of course, there's mobile.
 This tutorial will show you on the right way to see PLDT Wifi password that is inside the sign range. Basically we are going to install a software check this out in your Android machine, any Android model will do but for best end result it is best to have a minimum of Android OS 2.2 or later.
Nowadays, many Wifi accesses can be found in all places. But most of them are secured by a password that is difficult to get. The one solution to get it is to hack the Wifi network password. Certainly, our Wifi password hacker will help you to resolve your problem with one hundred% can download our Wifi hacker right now totally free and connect to any of the networks detected by your LAPTOP wi-fi community card. It is very useful for you especially in case you have temporary internet access. Stop risking your career! Use our software program that doesn't let any traces and that avoid any type of issues.
This tutorial will show you on the right way to see PLDT Wifi password that is inside the sign range. Basically we are going to install a software check this out in your Android machine, any Android model will do but for best end result it is best to have a minimum of Android OS 2.2 or later.
Nowadays, many Wifi accesses can be found in all places. But most of them are secured by a password that is difficult to get. The one solution to get it is to hack the Wifi network password. Certainly, our Wifi password hacker will help you to resolve your problem with one hundred% can download our Wifi hacker right now totally free and connect to any of the networks detected by your LAPTOP wi-fi community card. It is very useful for you especially in case you have temporary internet access. Stop risking your career! Use our software program that doesn't let any traces and that avoid any type of issues. Let's begin with updating the firmware. From the web interface, after you log in, you will find an “Improve” link close to the highest, together with several other navigation hyperlinks. Click on on Improve after which click on “Check for Upgrades”. If a more moderen version of the firmware is offered, you may have the option to flash the newer model. For those who choose to, you also have the option to manually download firmware and improve by copying the “.bin” file to the Pineapple.
Wifi hacks like that aren't the one safety threat we face. Street warriors looking to go online to their accommodations' wi-fi Internet can unknowingly become online mugging victims. In 2010, The CBS Early Present had an moral hacker set up a fake wifi entry level at a New York City lodge, calling it “Greatest Free Public Wifi.” Before lengthy, dozens of unknowing wireless users took the bait and tried to go browsing. When an unsuspecting lodge visitor connects to a phony wifi access level like that, his bank card, banking or different confidential enterprise info will be seen by the hacker.
Let's begin with updating the firmware. From the web interface, after you log in, you will find an “Improve” link close to the highest, together with several other navigation hyperlinks. Click on on Improve after which click on “Check for Upgrades”. If a more moderen version of the firmware is offered, you may have the option to flash the newer model. For those who choose to, you also have the option to manually download firmware and improve by copying the “.bin” file to the Pineapple.
Wifi hacks like that aren't the one safety threat we face. Street warriors looking to go online to their accommodations' wi-fi Internet can unknowingly become online mugging victims. In 2010, The CBS Early Present had an moral hacker set up a fake wifi entry level at a New York City lodge, calling it “Greatest Free Public Wifi.” Before lengthy, dozens of unknowing wireless users took the bait and tried to go browsing. When an unsuspecting lodge visitor connects to a phony wifi access level like that, his bank card, banking or different confidential enterprise info will be seen by the hacker. This penetration testing platform is for many who are going to start penetration testing of Android functions. All you need is to download the AppUse Digital Machine and then load the app for testing. The app comes with a lot of the configuration. So, you do not want to install simulators, testing instruments, no need for SSL certifications of Proxy. Thus, the tool gives best user expertise. In different phrases, you can say that AppUse Digital Machine is Backtrack for Android apps. As we all know that world is moving in the direction of apps, AppUse VM has a superb scope in future. We see how Android customers face assaults and these cyber-attacks are rising. So, it will be important for all Android app developers to test their apps for various kinds of vulnerabilities.
This penetration testing platform is for many who are going to start penetration testing of Android functions. All you need is to download the AppUse Digital Machine and then load the app for testing. The app comes with a lot of the configuration. So, you do not want to install simulators, testing instruments, no need for SSL certifications of Proxy. Thus, the tool gives best user expertise. In different phrases, you can say that AppUse Digital Machine is Backtrack for Android apps. As we all know that world is moving in the direction of apps, AppUse VM has a superb scope in future. We see how Android customers face assaults and these cyber-attacks are rising. So, it will be important for all Android app developers to test their apps for various kinds of vulnerabilities.
